Working as a team member in a vulnerability management program
Working as a team member in a vulnerability management program requires collaboration, communication, and coordination with other team members. Make sure you understand the program objectives and have a clear understanding of the goals and objectives of the vulnerability management program. This includes understanding the scope of the program, the types of vulnerabilities being addressed, and the overall strategy and timeline.
- Vulnerability management is a team effort, so it's important to collaborate with other team members. This includes working closely with vulnerability analysts, IT administrators, security engineers, and other stakeholders to identify, prioritize, and remediate vulnerabilities.
- Communicate effectively: Communication is key in any team effort. Ensure that you communicate clearly and effectively with other team members. This includes providing regular updates on the status of vulnerabilities, sharing relevant information and insights, and discussing any challenges or issues that arise.
- Follow established processes and procedures: Vulnerability management programs often have established processes and procedures in place to ensure consistency and efficiency. It's important to follow these processes and procedures to ensure that vulnerabilities are addressed in a systematic and organized manner.
- Share knowledge and expertise: As a team member, you likely have unique skills, knowledge, and expertise. Share your insights and ideas with the team to contribute to the overall success of the program. This could include sharing information on emerging threats, new vulnerability scanning tools or techniques, or best practices for vulnerability remediation.
- Be proactive and take ownership: Take ownership of your assigned tasks and responsibilities. Be proactive in identifying and addressing vulnerabilities, and take the initiative to contribute to the overall success of the program. If you encounter challenges or obstacles, be proactive in finding solutions and seeking assistance from other team members when needed.
- Stay up-to-date with industry trends: Vulnerability management is a rapidly evolving field, with new vulnerabilities and threats constantly emerging. Stay updated with the latest industry trends, research, and best practices to ensure that your team's approach to vulnerability management is effective and up-to-date.
- Foster a positive team culture: Building a positive team culture is essential for effective collaboration. Foster a collaborative and supportive environment by being respectful, open to feedback, and willing to help other team members. Celebrate team successes and learn from failures to continuously improve the vulnerability management program.
By following these tips, you can work effectively as a team member in a vulnerability management program and contribute to the success of the overall program. Remember, teamwork is crucial in vulnerability management as it requires a collective effort to identify, assess, and remediate vulnerabilities to protect an organization's assets from potential threats.
Searching for issues
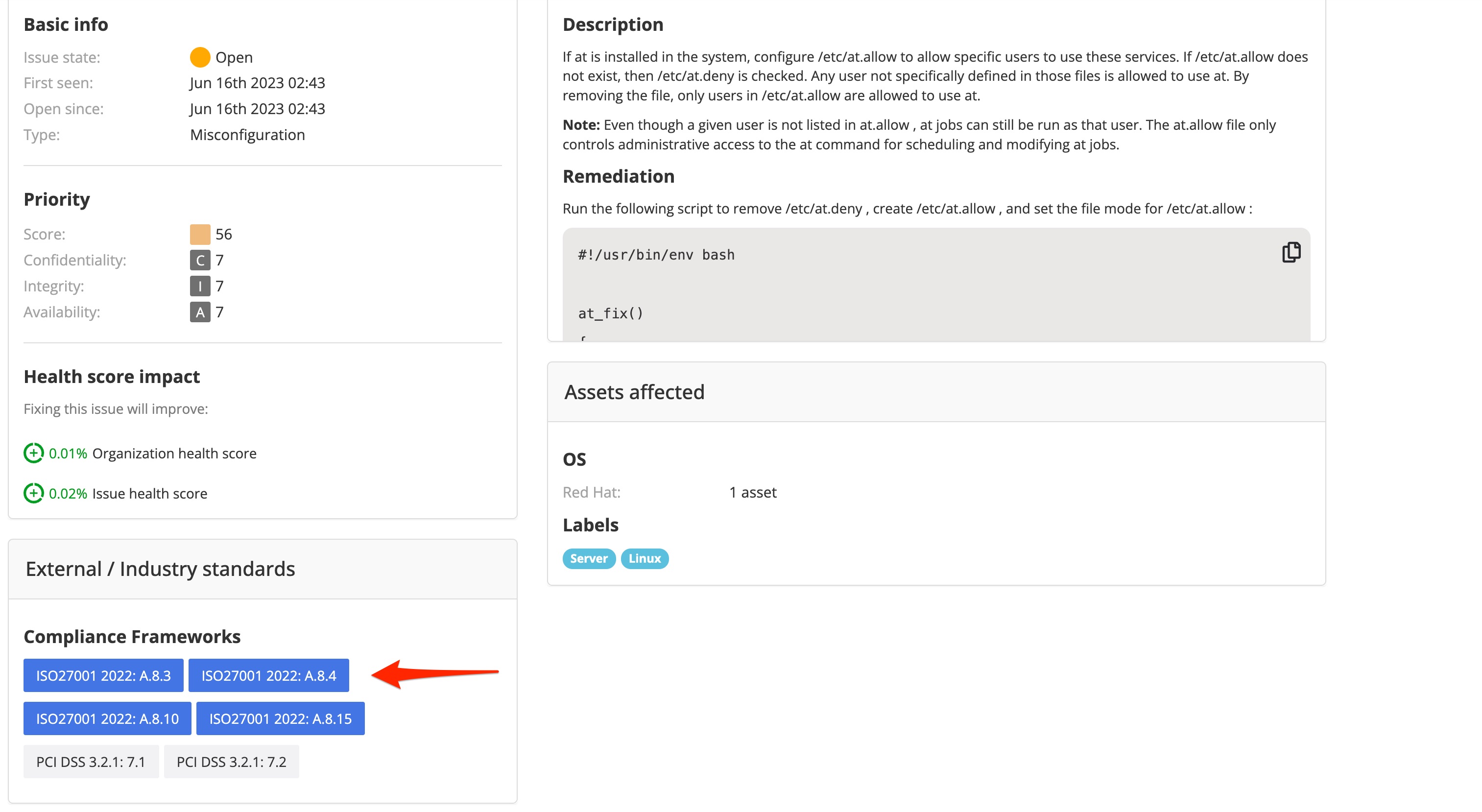
A detected issue by Nanitor is a potential security threat. Nanitor detects thousands of issues of various severity and origins. An issue can be a vulnerability in an installed software or operating system, a misconfigured operating system, too widely granted user permissions, or an undesired open port just to name a few. All issues get a prioritization score based on the priority of an asset that has been detected based on the best available information from the issue itself. Issues are by default sorted with an ascending order of the prioritization score helping system administrators to spot and focus on issues that have a huge impact on the cyber security of an organization.
But looking at issues with the highest prioritization score is not always the desired way since the remediation of top prioritized issues needs to be handled from different angles. You as a system administrator or appliance manager or database manager need to look at issues that are of your concern and are within your responsibility and your sphere of influence. Therefore it is essential to understand the dimensions of an issue and the parameters available that can be leveraged to search for the issue of your concern.
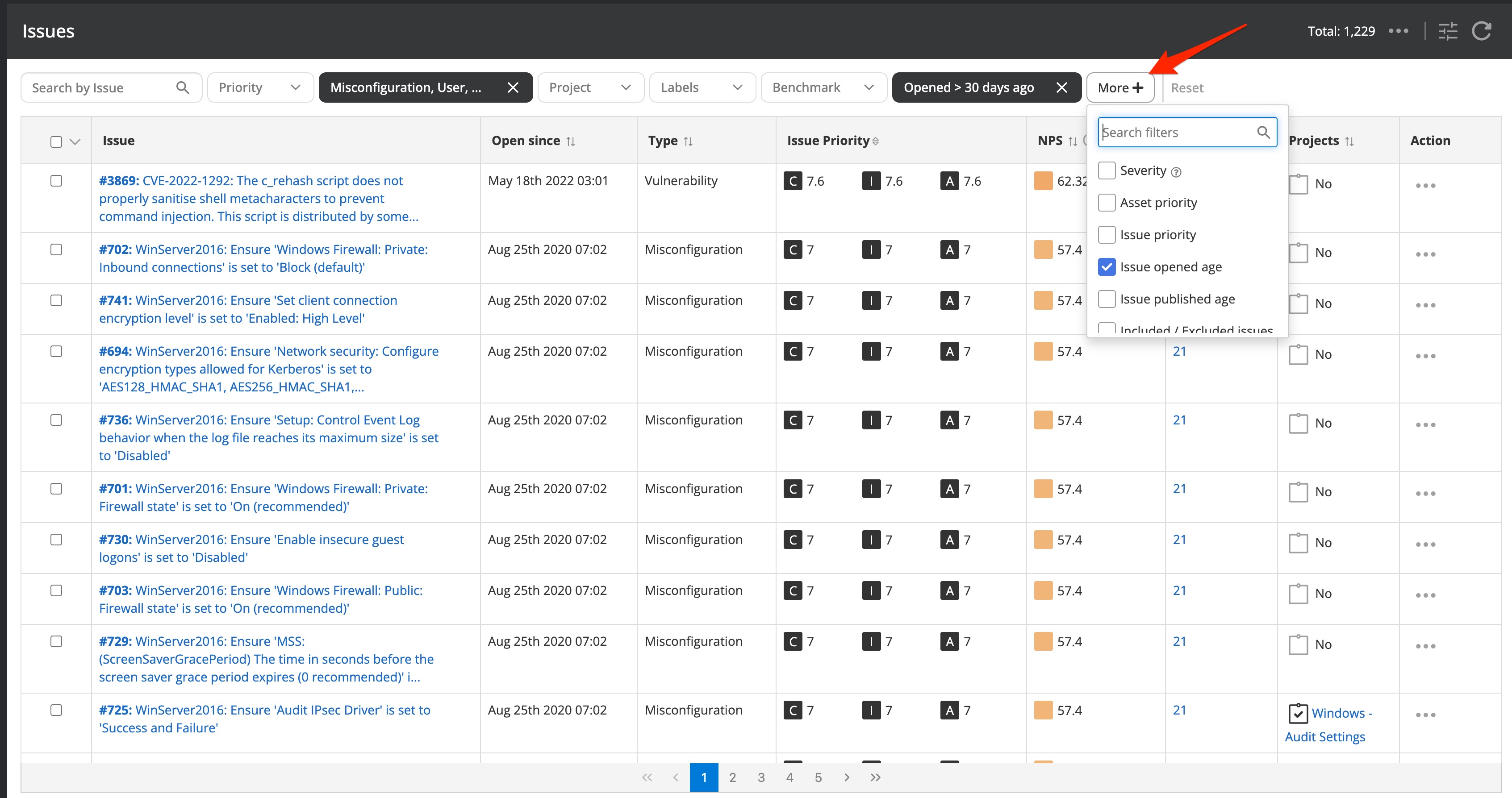
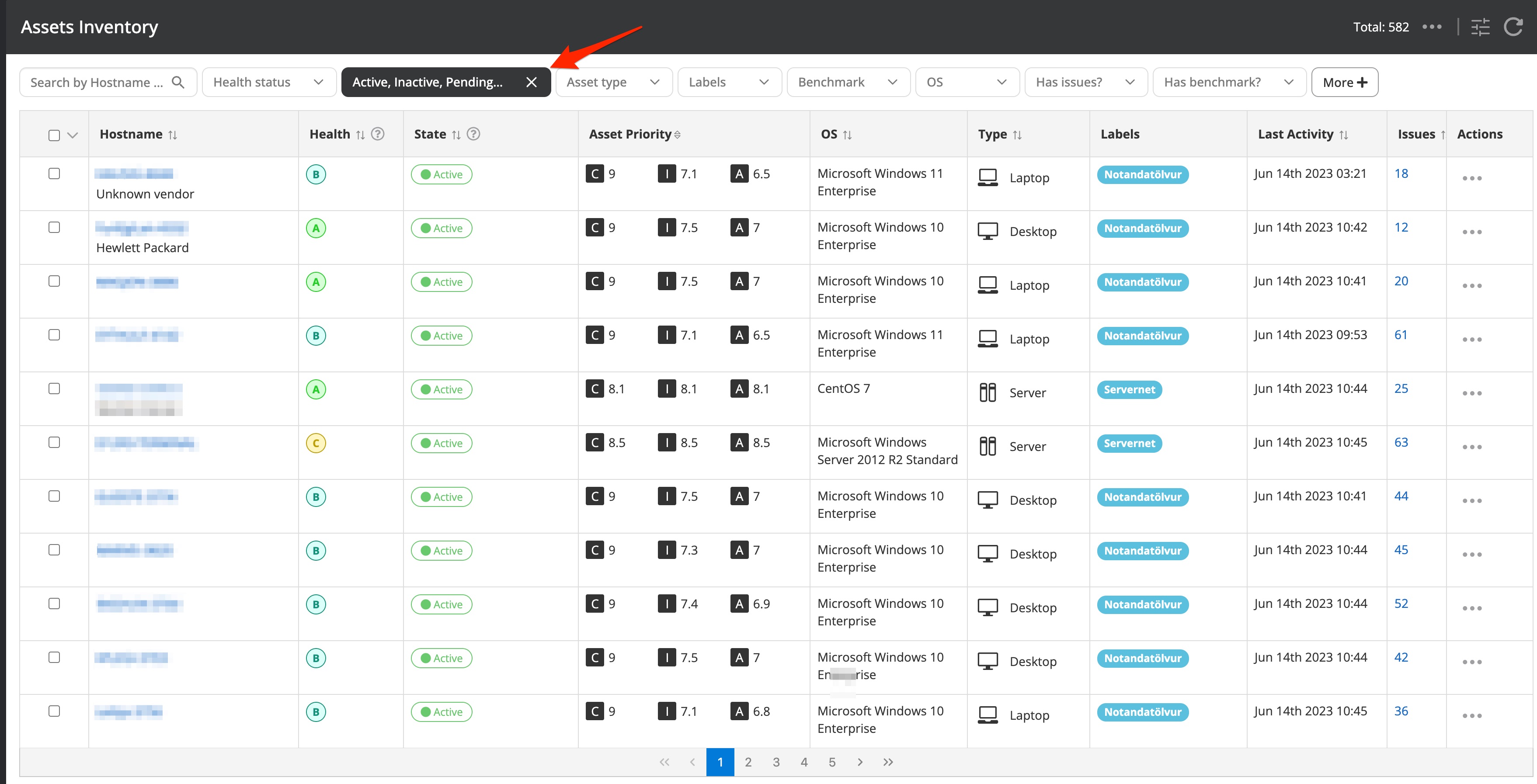
Navigating to the list of detected issues by selecting Issues → list will show an unfiltered list of the detected issues. The filters on the top of the issue list can be leveraged to minimize the list to issues of your interest.
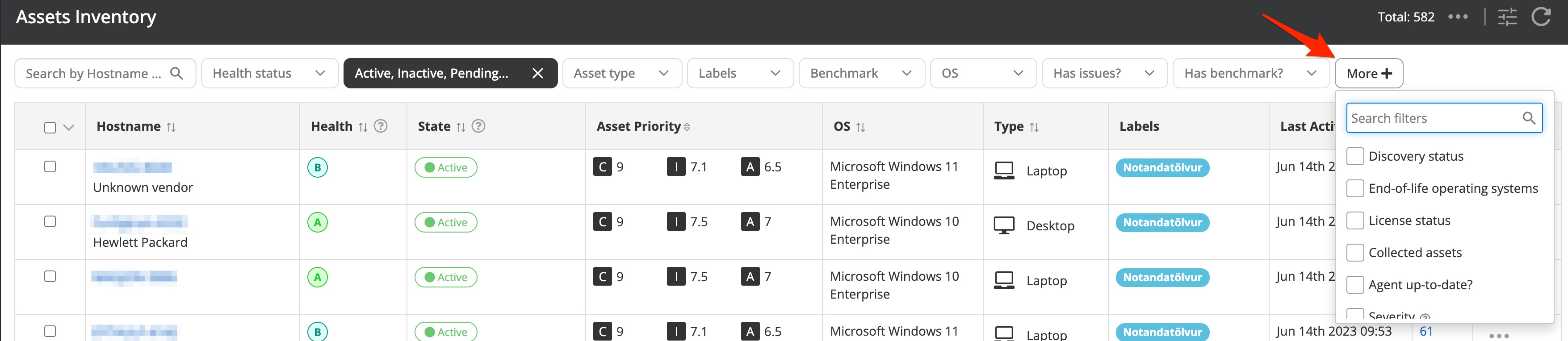
It is important to notice that there are some default, commonly used filter options visible. Additionally, you have the option to leverage further issue filter options available from the "More" button. Once an additional filter option is selected you can choose an available and suitable value to filter on. Be advised that you will always need to press the "Apply" button to activate the selected search options.
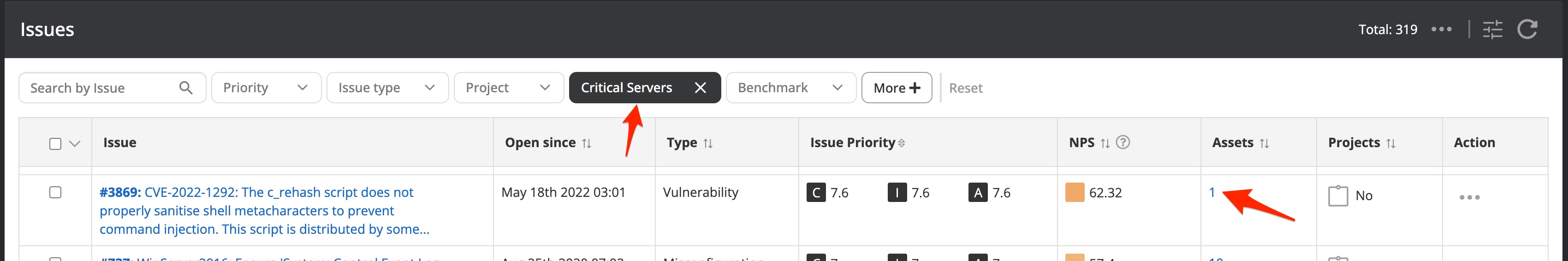
Besides the default available options to search for in Nanitor, you should create your own scope of issues detected on assets that belong to your authority. That can be achieved by creating labels. When you apply a label (one or more) filter the issue list will not only be limited by the filter, additionally, the number of assets where the issue has been detected will be reduced to the number of assets that are within the scope of the filter(s) that have been applied in the search.
There are two different kinds of filter options for issues. One that is limiting the number of assets. From the use case above we can see that this applies to the label filter options but also other asset-related issue filter options such as:
- Labels
- Benchmark
- Platform
- Asset priority
Other filtering options do not limit the search to the number of assets. There are multiple search parameters that apply only to issues. It is important that you understand the available options since they can help you to focus on issues of your interest. If you have not done so already it is recommended to read the article about labels to get a good knowledge of used dimensions in Nanitor such as issue priority, issue types, and the issue prioritization score just to name a few. It is also recommended you get familiar with the issue opening date since it might be useful to filter issues that have been newly detected in the last couple of days.
The complete list of available options related to issues are:
- Projects. Remediation projects are an effective way to increase your organization's health score in an organized way and track progress against your scheduled remediation work.
- Priority. The priority refers to the issue prioritization score and is divided into issue priority groups.
- Issue Priority is the dynamic priority of an issue.
- Issue types
- Issue severity is another perspective to looking up high-risk issues. The issue severity is drawn from multiple angles depending on the type of the issue. For E.g. the severity of a vulnerability is defined by the CVSS score of the vulnerability whereas the severity of a misconfiguration issue is set by the team of security experts of Nanitor. The severity of User issues or device issues can be set by an administrator of Nanitor in Organization Management → Settings → Issues.
- EPSS score or Exploit Prediction Scoring System is a measurement of liklyhood of exploitibility.
- Other filtering options that refer to vulnerability issues only:
- CVSS (or Common Vulnerability Scoring System) base score
- CISA-known exploits
- CVSS vector
- Included/Excluded issues. This option is helpful to identify issues that have fully or partially excluded for any reason by you or others
Be advised that applying multiple issue parameter filters work as an AND operator. The issues returned in the list need to match all selected search parameters.
Lookup non-detected vulnerabilities
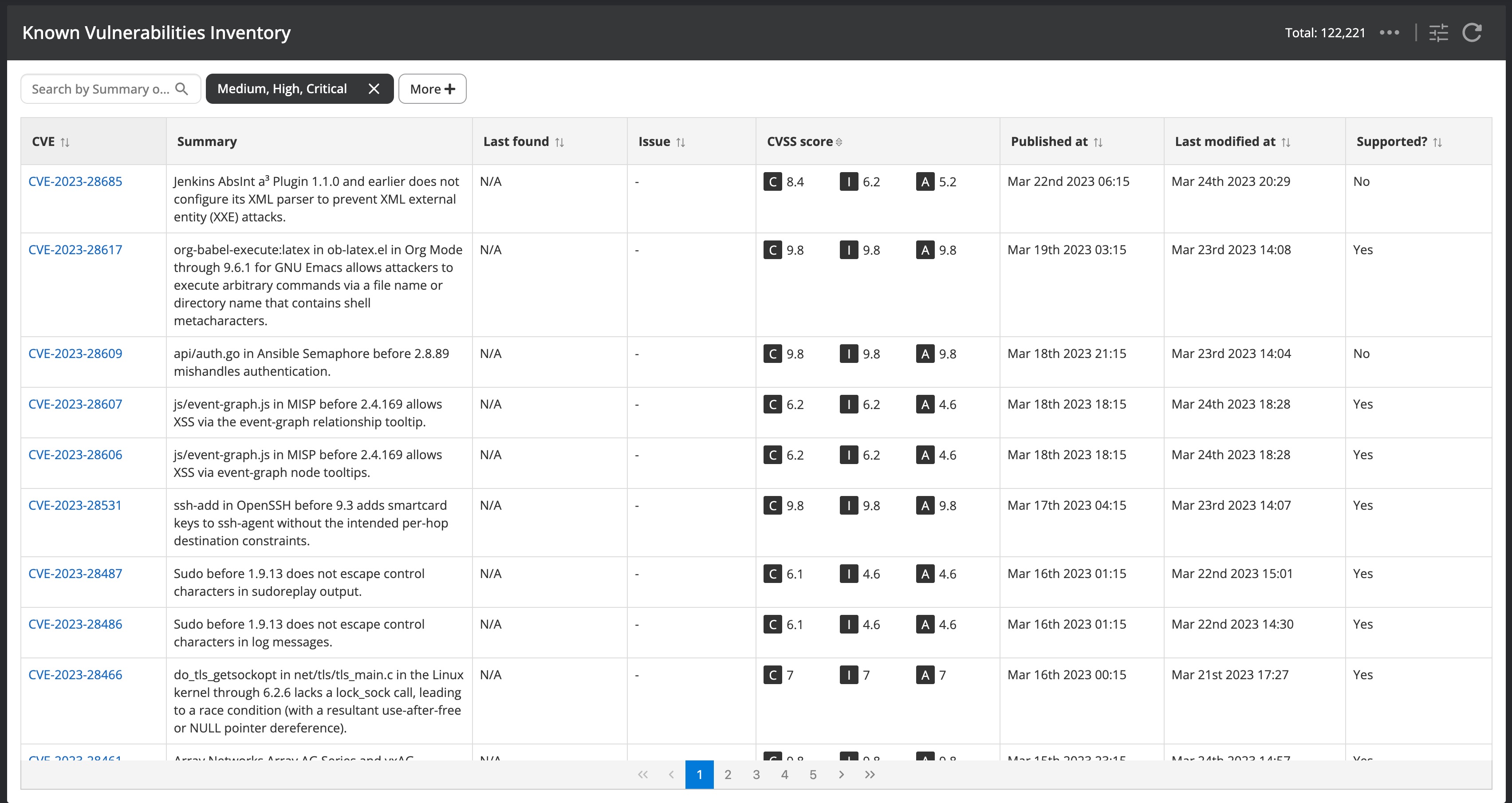
Besides the ability to search on detected issues, you might also be interested in knowing if a certain vulnerability can be in general detected by Nanitor. Nanitor maintains a source list of vulnerabilities more detailed are these vulnerabilities with a CVE number issues by the MITRE cooperation. This list of those vulnerabilities can be viewed by navigating to Inventory → Known Vulnerabilities.
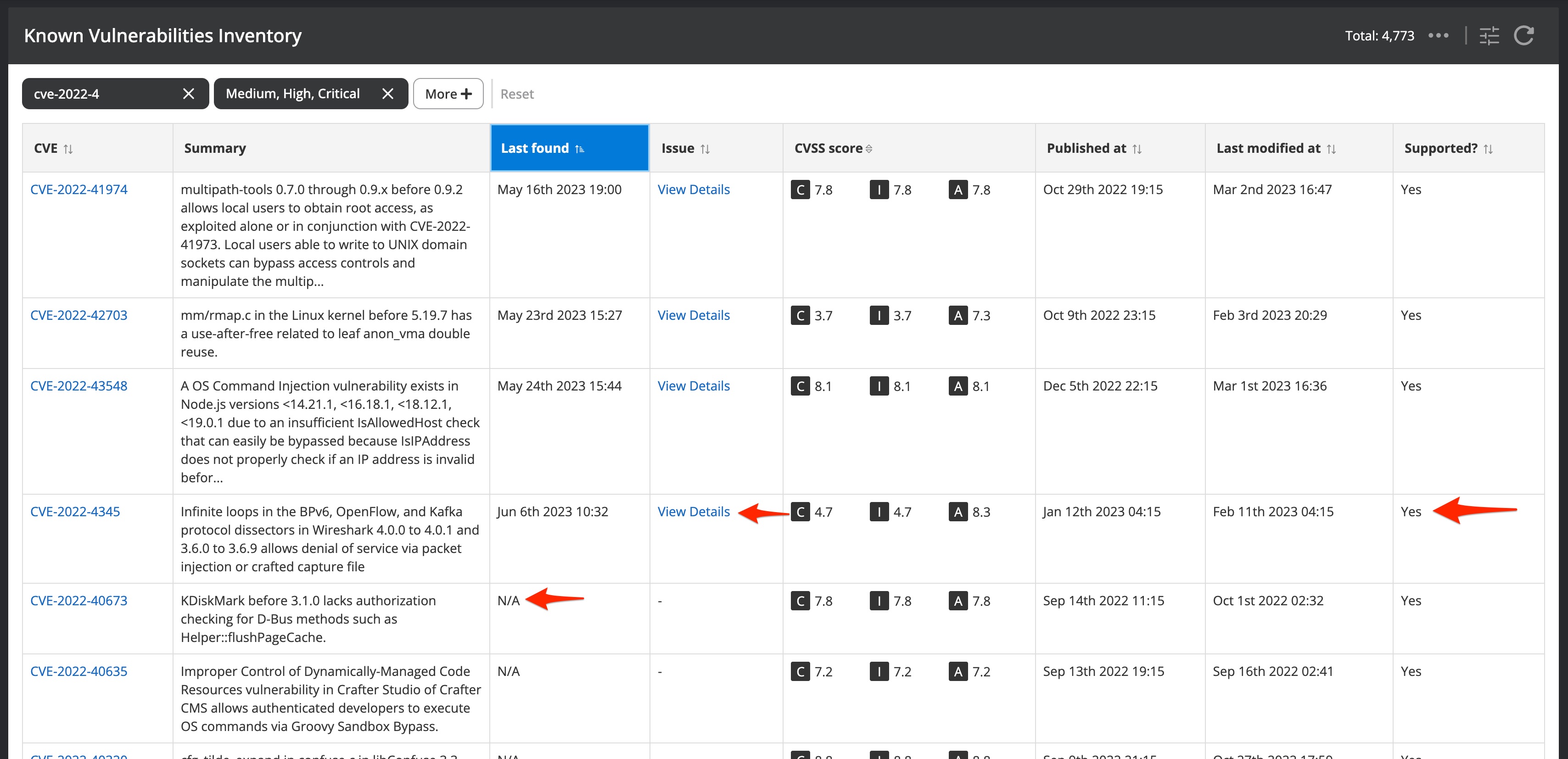
At the point of writing, there are more than 200 thousand known vulnerabilities. The default list in the screenshot above is filtered on medium, high, and critical vulnerabilities only. You can search for a recognized CVE number of your interest by leveraging the search option. Nanitor will tell you if a vulnerability has been detected within your monitored assets and display the date of its last detection including a link to the issue itself where more detailed information can be gathered.
The support column will also tell you if a detection method is available within Nanitor.
Vulnerable software
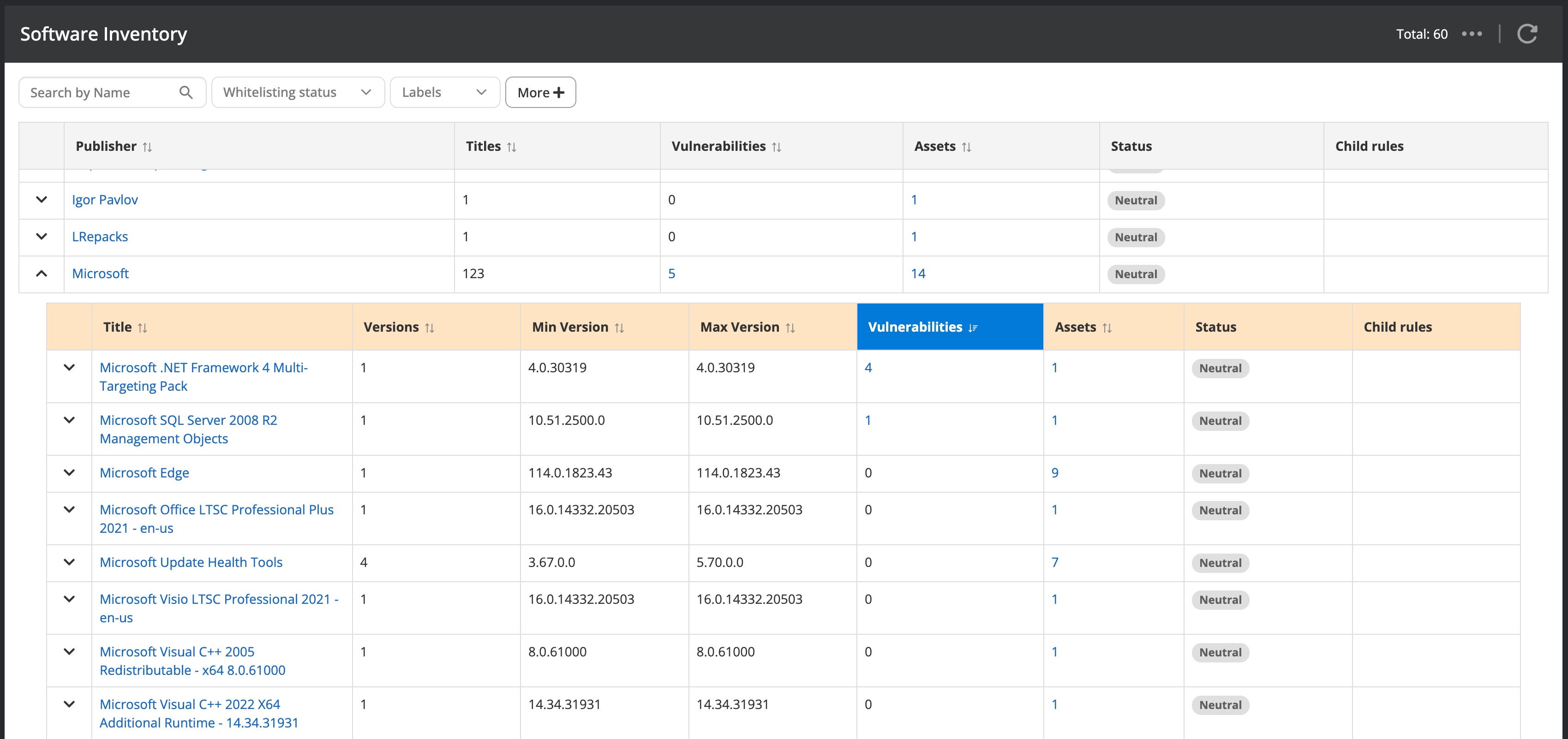
Nanitor keeps track of all installed software on your assets and can be considered a software asset management (SAM) platform. Navigating to Inventory → Software will bring up a list of installed software across your organization. The software inventory list is grouped by the Software vendors, the software title, and the installed versions of the software.
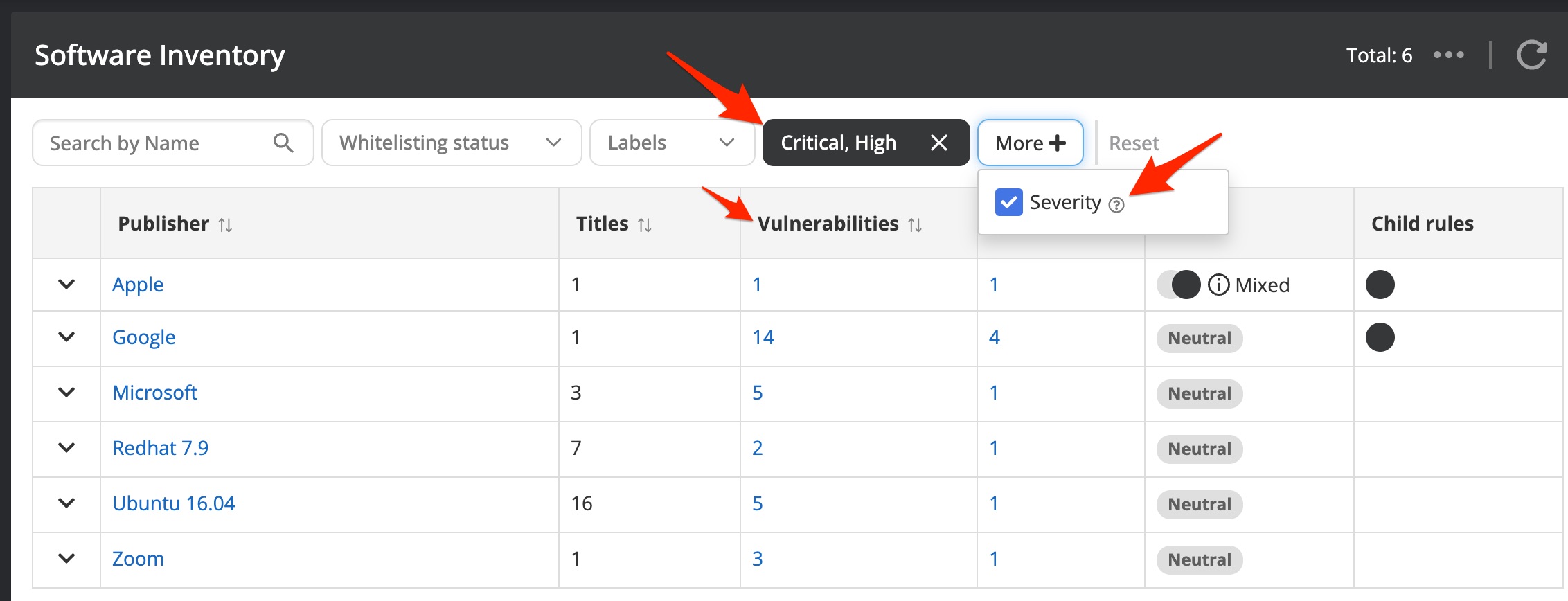
The populated software inventory helps to identify unwanted software and software with outdated versions by blacklisting software. Further, you can define mandatory software that needs to be present on all your assets. Having a software policy in place is not only making you more secure, but it also reduces patching efforts by removing repeatedly vulnerable software. You can identify vulnerable software by applying the severity filter option. After applying the filter you will a list of software with vulnerabilities of the severity grade that you have specified.
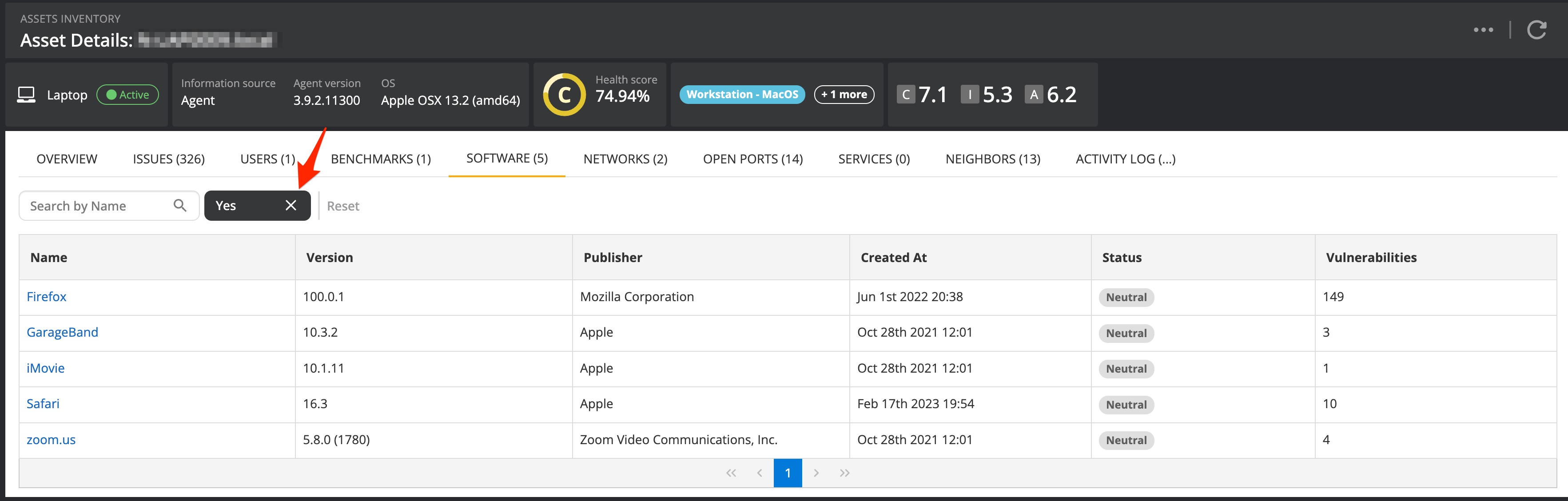
The same approach can be applied when looking at specific assets. The asset view lists the installed software. When you apply the "Has vulnerability" filter you will get a list of software with existing vulnerabilities indicating that this software needs to be patched.
Compliance issues
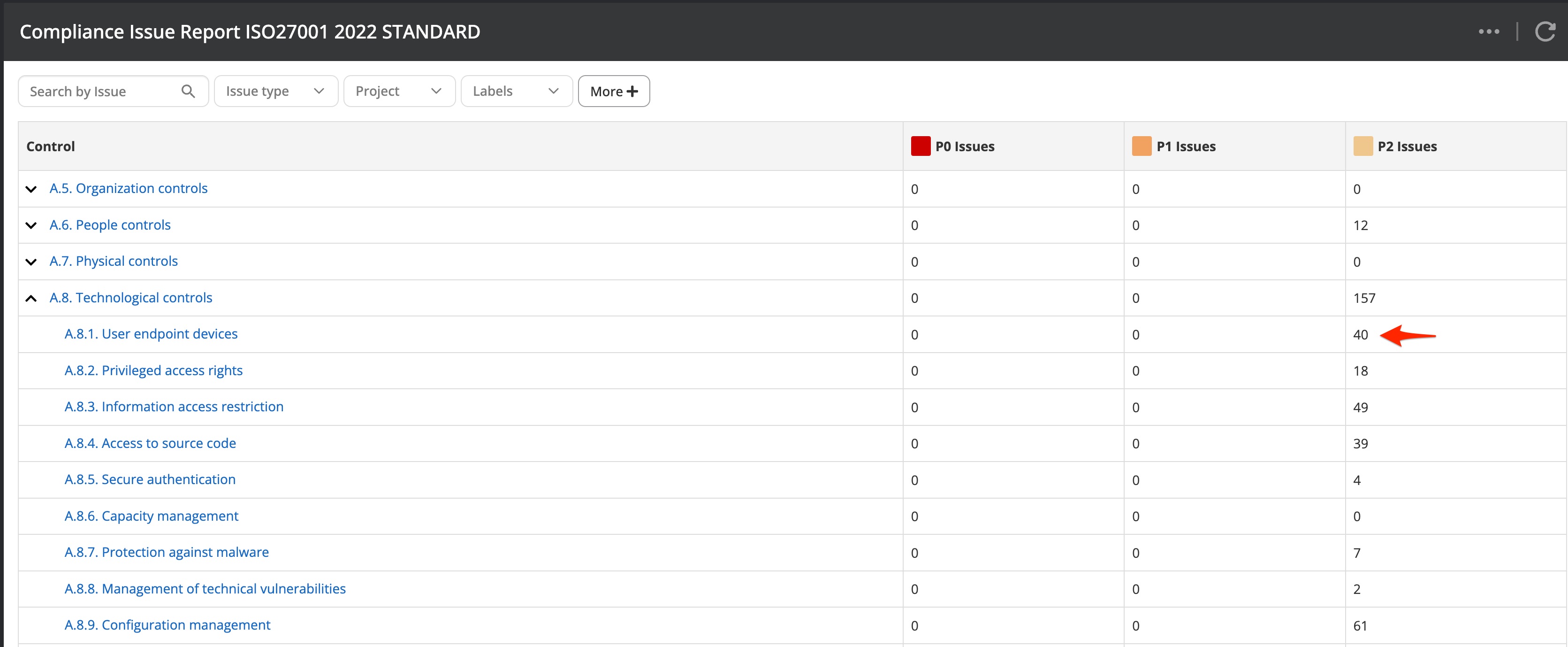
Many if not most of the companies caring about cyber security do have additional requirements to fulfill from external institutions. Certifications like ISO27001 or PCI-DSS have a lot of requirements that concern cyber security. Nanitor supports a wide range of compliance frameworks in the sense that a detected issue will get matched to a compliance framework and a referring chapter within that framework. You can view relevant issues to the compliance framework you need to comply with by navigating to the Reports → Compliance issue report.
The Compliance issue report shows all relevant chapters and subchapters of the compliance framework and matches detected issues to one or more chapters if they apply. The matching is done by Nanitor security experts. Within the details of a detected issue, you can see what compliance frameworks the issue matches to.
Keeping the list of compliance issues empty is an important target for every compliance and security officer and can be used for auditing purposes.
Viewing assets managed by my team
As a member of a cyber security team, you need to have a comprehensive overview of available assets within your organization. Nanitor can provide you with this view when you have installed and distributed the Nanitor agent on your assets. For other assets where an installation of an agent is not feasible, you can connect to that asset by leveraging a Nanitor collector. Due to its network discovery functionality, Nanitor will not only display/list assets with a client (agent or collector) but also detected assets on your networks seen by the Nanitor agents. You need to choose for which discovered networks you want the network discovery to be enabled.
The complete list of assets can be viewed by navigating Inventory → Assets
The default view shows all assets besides archived ones. Archived assets are assets that have been decommissioned or stopped reporting into Nanitor longer than the threshold of the asset archival policy (can be adjusted under Settings → Organization Management → Asset Archival). It is fundamental to understand the various states an asset can be in.
Similar to searching for issues you can leverage various filtering options to view assets of your interest. Clicking on the more button will reveal the full list of options to filter on.
Commonly used and useful filter options for assets are:
- Asset type
- Asset health status to identify weakly secured assets
- Asset label(s) to find assets related to a resort (group of assets) that are defined by a labeling rule or assigned manually
- Applied (CIS) Benchmarks
But there are also other filter options that help you to identify problematic assets in the sense that Nanitor is not capable to retrieve all relevant, up-to-date information. Therefore a problematic asset is a potential security concern. You should regularly perform an asset reporting health check to ensure that all clients can perform the most recent checks and deliver up-to-date information about the asset itself.
- Agent-up-to-date will filter on all assets that have an outdated client. Think of it like a missing patch on an asset. Usually, the agents should upgrade themselves if the self-upgrade option is enabled (can be enabled under Settings → Organization Management → Settings → General) but there might be various reasons why this process is failing
- Assets with no benchmark show assets where Nanitor is not capable to match a (CIS) benchmark to the asset. The reason for a missing benchmark is in most cases an outdated agent version. But if the agent is up to date you should create a support request in our customer portal. When Nanitor fails to assign a benchmark to an asset, a security configuration check is not possible. As a consequence, you might get a false positive configuration health score for the asset.
- Asset activity problem should indicate any hints for problematic assets that would need your attention eg when an asset fails to check-in
Besides leveraging the asset filter options you can also use the available columns in the asset list to sort in an ascending or descending order if the available column allows such a sorting.
You can adjust the visible asset columns and re-arrange their order from the customize icon on the top right.
Depending on your use case you might leverage the asset inventory in Nanitor as an asset management tool or look for weak assets or ensure that all of your assets are correctly captured to ensure Nanitor findings are correct and reliable.
Remediation projects
An important part of increasing the organizational cyber security health status is to organize the remediation efforts across teams. A transparent tool is needed to capture decisions from the findings of vulnerabilities in Nanitor and make collaboration on cyber security efforts within your organization possible. The project module within Nanitor is a suited tool to organize remediation work. A project in that sense might not necessarily mean fixing a vulnerability with an update or adjusting a setting or upgrading the operating system to a maintenance-supported system, but there is often some due diligence needed to decide and investigate how applicable a detected vulnerability is, what the possible impact of a remediation of a vulnerability is by applying a patch or a software update as it might break running applications or services. Nanitor's project capabilities are tailored to the needs to run and manage a vulnerability program since it is not only to remediate existing vulnerabilities but it can also help you to define the target for assets to onboard or setting a target health score for your assets. To get more familiar with Nanitor projects, what they are exactly, a best-practices guide, and how you can leverage projects for reporting purposes it is advised to go through the remediation chapter or the in-depth knowledge base article.
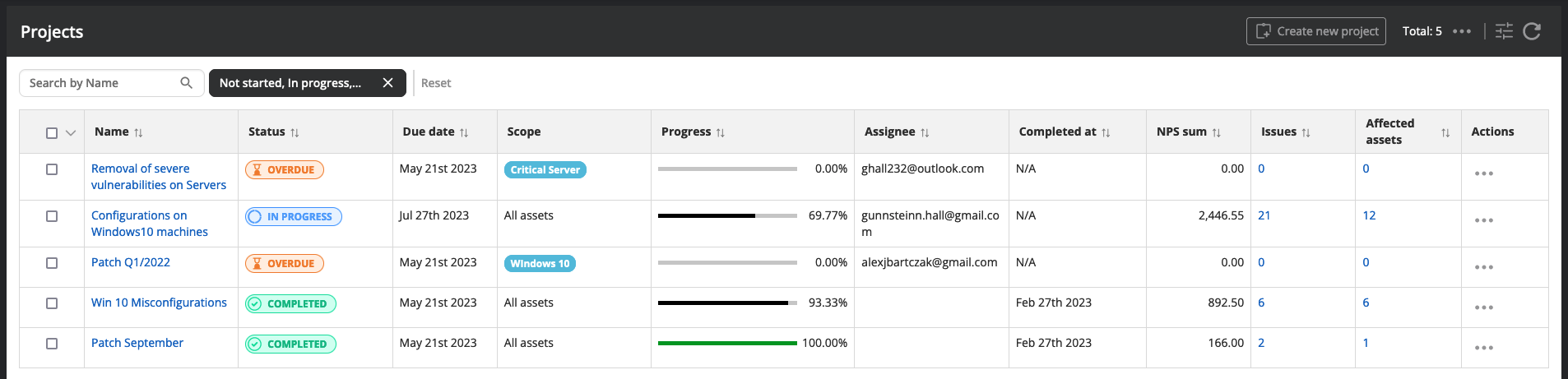
The list of remediation projects can be accessed from Issues → Projects
A remediation project is a commitment to remediate or do some due diligence on detected vulnerabilities, or organize the onboarding of your assets into Nanitor. You need on a regular basis catch up with the decision you or your team made and track the progress against your projects and make adjustments if needed in a timely manner. Remediation projects should be discussed in team meetings or other collaborative tools. Watch out for:
- Ownership of remediation projects is clearly defined and leaders are aware of their responsibilities. You should set up a notification rule for any changes in the project scope to be aware when changes in scope are happening in projects you are responsible for or issues are getting resolved in your projects.
- Due date is reasonable according to resources available and the scope of a project. Adjust the scheduled delivery date to reflect changes
- Progress should be in accordance with the elapsed time since the project started. Limit the scope or add resources (if available) when progress is below expectations or is likely to not hit the target date. It might be unrealistic to complete a project 100% and a project stays at a rate above 95%. In those cases, it is advisable to shut down the project (by archiving it) and create a new one with the remaining outstanding issues.
- The project scope is defined but the number of issues in a project and the number of assets (defined by labels) the issues should be remediated on. It is strongly advised to start off with a very limited scope to identify for yourself what you are capable to deliver.
- The NPS scoring points (NPS sum) of a project is indicating the impact on the organization's health score when remediated as it factors and sums all issue priorities with all asset priorities included in a project.
- Project comments help to communicate between teams and team members which makes decision and communication processes transparent and increases efficiency. Comments can be added and resolved if they involve a decision or a task to perform.
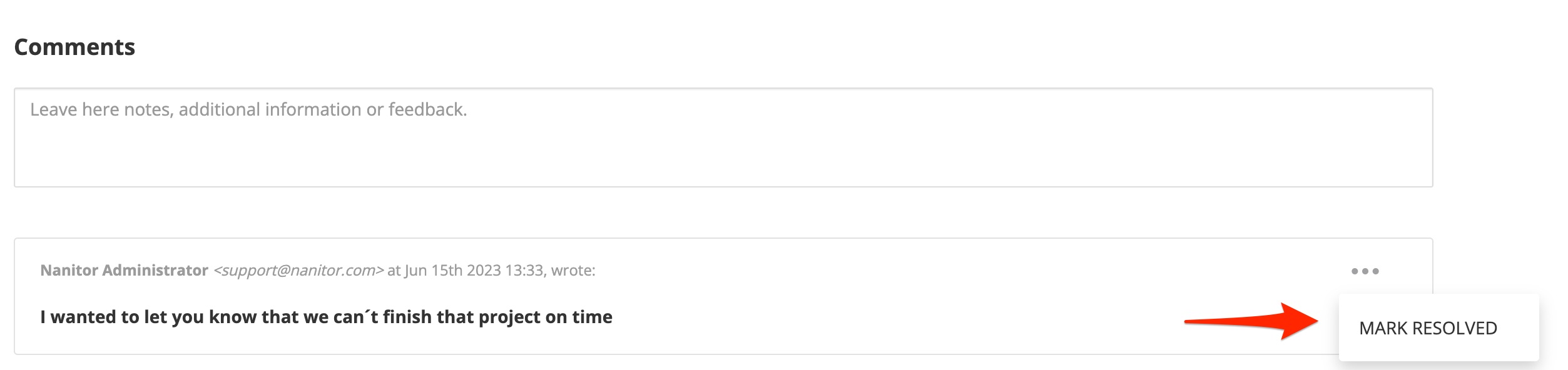
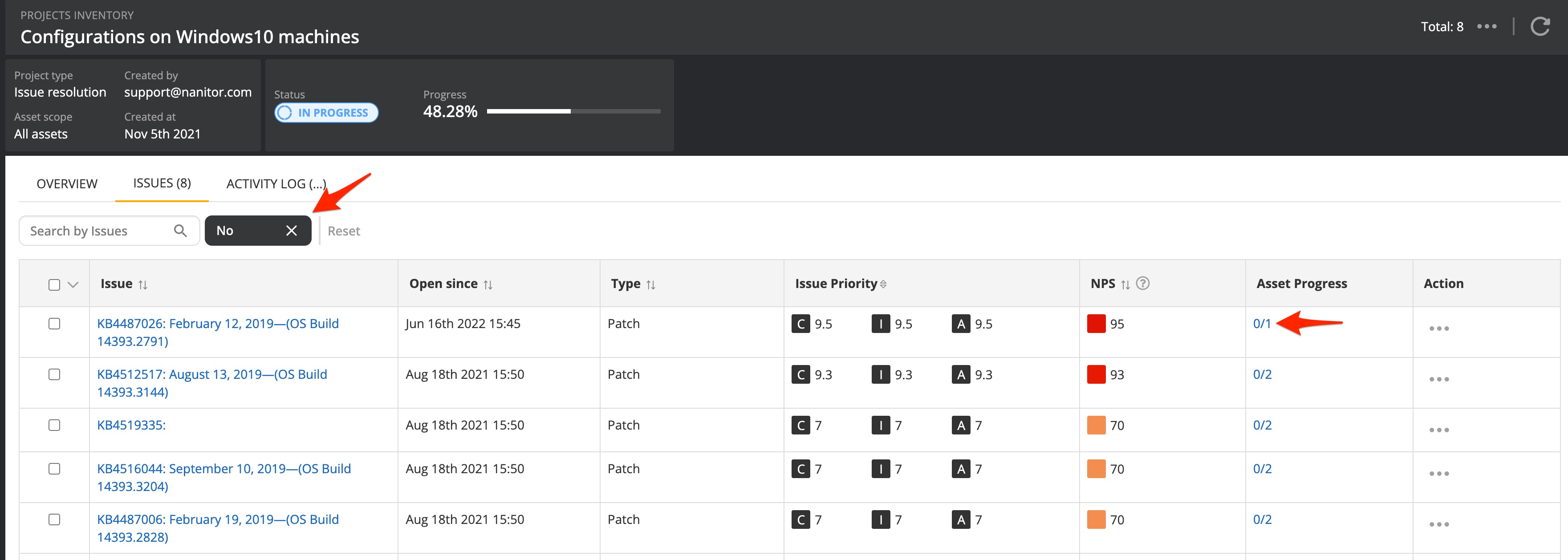
In a Nanitor project, you will also be presented with a view of included issues in your project. The view will list both still-existing and resolved issues. Resolved issues are formatted with a strikethrough. To track down still to resolve issues you can leverage the Resolve filter parameter.
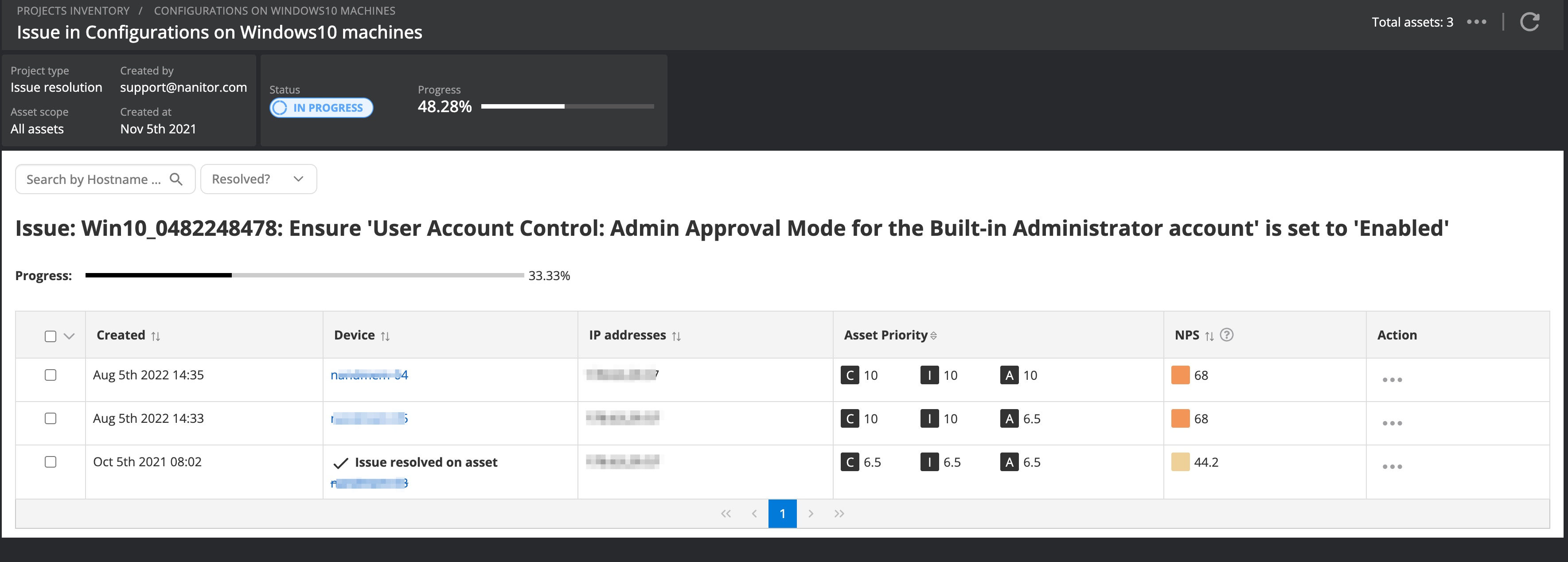
This will bring up a list of remaining issues in the remediation project. The asset column will also indicate how many assets the issue already has been resolved on. Clicking on the link will lead you to the details of the asset list for that issue.
Having all that in mind Nanitor is the perfect tool to manage remediation work integrated into the detecting platform itself. But establishing integrations to other platforms is achievable with a ticket system that supports reading from an email account. A native Jira integration is about to come.
Prioritizing vulnerabilities
The core task of a team member of a cyber security program is to hunt down detected vulnerabilities. They pop up like moles. You can never stop and rest on your achievements. You can not defeat them all but you can focus on those that are the most important ones and those who have the biggest impact on the IT security health of your organization.
Nanitor detects thousands of issues and therefore it is essential to focus on issues that matter the most to your organization. The priority engine included in the Nanitor software helps you to identify the most important issues that you need to take care of. There are many parameters that matter and some are more relevant to the field you are specifically working on. You might need to focus on hardening the security configuration of your operating systems, patch all relevant software titles or remove granted user permissions. Refer to our quick start guide to give you an idea of where you should begin the remediation journey. But the entire house of cards is based on a holistic view of your asset fleet and therefore it is the first step that everything gets captured in Nanitor and all your assets are prioritized accordingly.
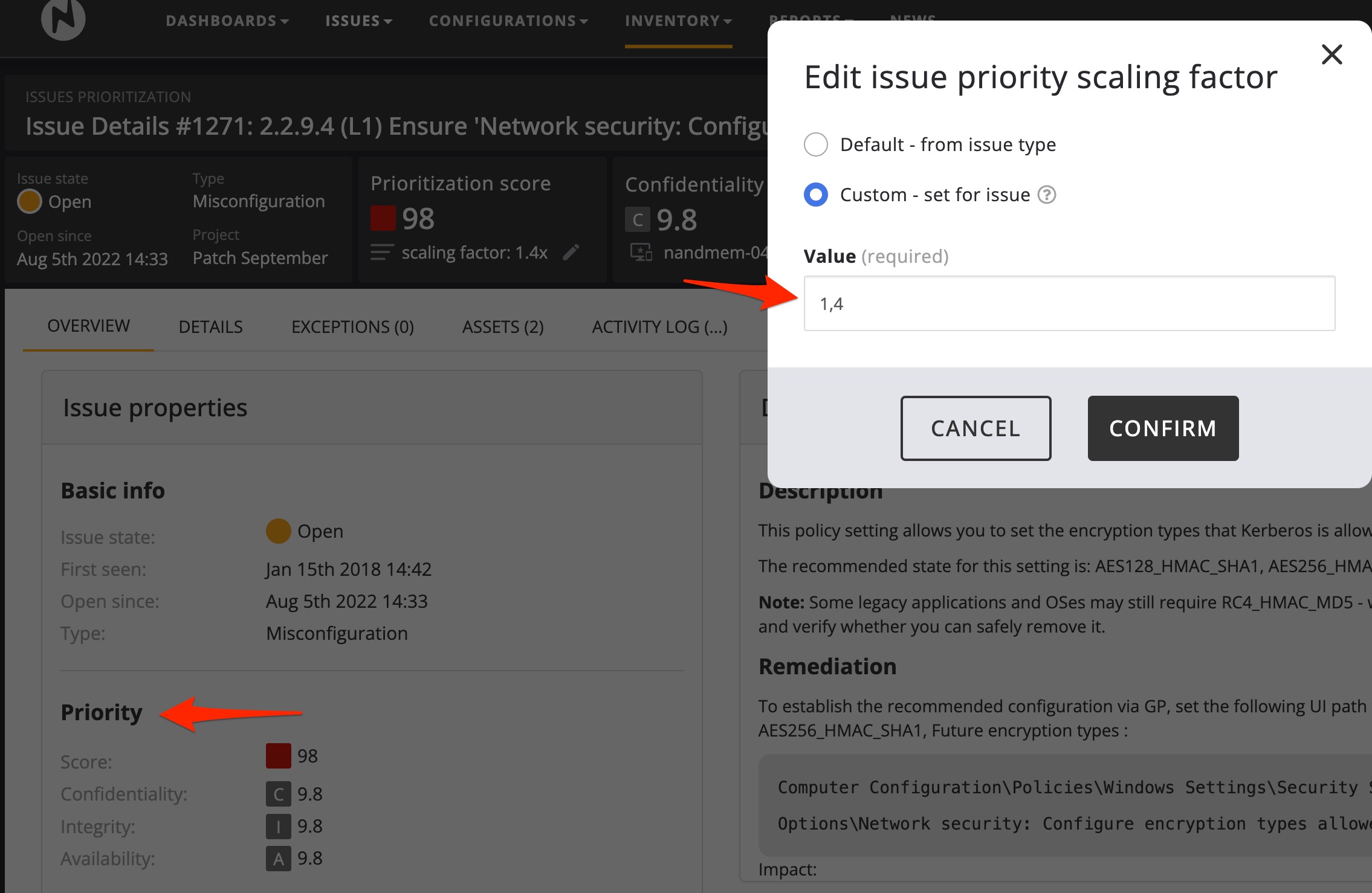
Nanitor has an intelligent scoring system for its detected issue and should be accurate on most occasions. However, each IT environment is different and some areas can be more important for certain businesses. For those cases, the issue priority rating does not reflect the real circumstances and needs adjustment. That can be achieved in Nanitor on a global basis for certain issue types (Organization management → Settings → Issues → Issue type priority scaling factor). A scaling factor will higher (or lower) the issue's priority. But instead of doing this on a global basis, it can also be done on the issue level by lifting (or lowering) the priority of a single detected issue.
Tracking vulnerabilities
Hunting vulnerabilities is not always fun. As soon as you killed one there will pop-up another one. It is continuous work to remediate vulnerabilities and patch your assets and the software that is installed on them. In that routine, you need to include checking on newly detected vulnerabilities in Nanitor but also verify that a hot-discussed vulnerability in the internet is captured by Nanitor and non-existing in your environment.
In the above sections, we have in detail covered various ways to identify and search for issues. Searching by the detection date (date opened) will always reveal a detailed list of detected issues within the last x days which you should always keep an eye on. This filter can be combined with other filter parameters to identify issues of your interest. The overview dashboard provides a comprehensive and holistic view of your vulnerabilities from different angles.
If you want to Nanitor do the work for you and send you information on newly detected or open vulnerabilities you should do so by creating a notification rule. Eg. a notification rule for P0 or P1 issues should exist in every organization.