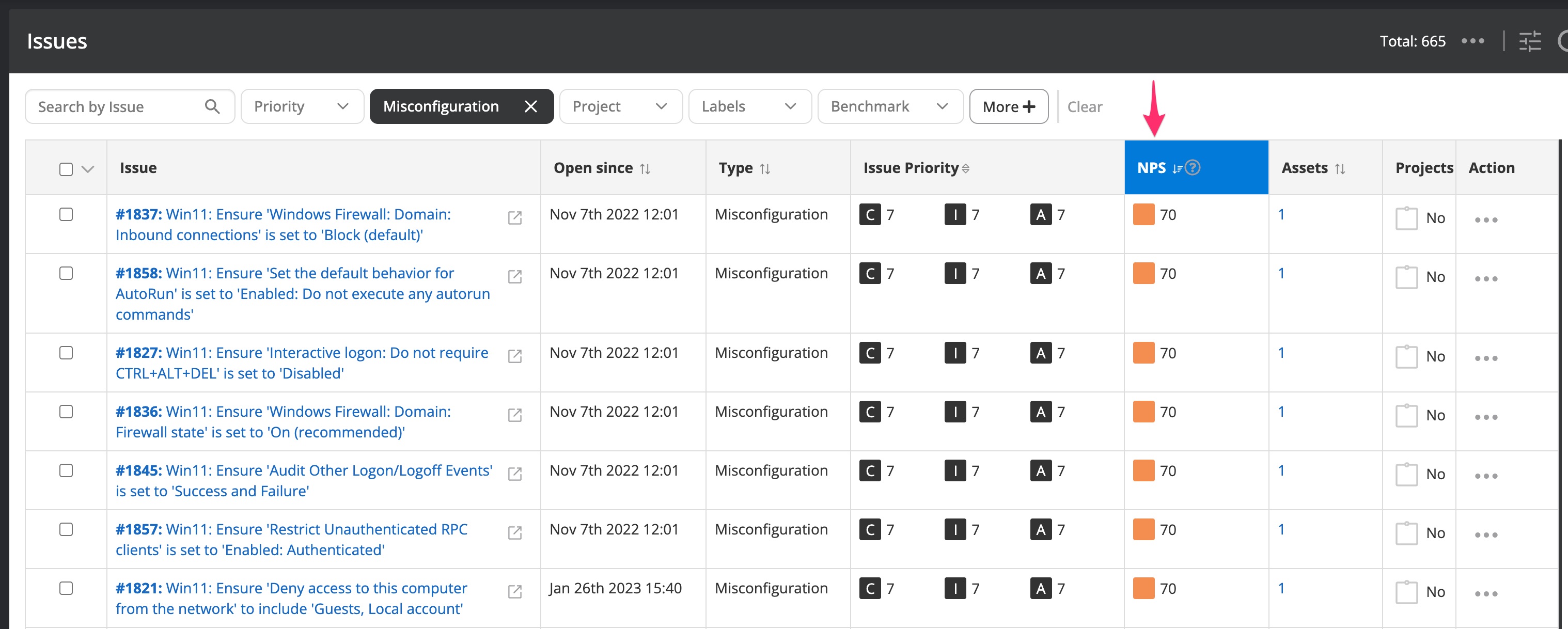
Issues overview
Within Nanitor, an issue is a potential problem with your system's security posture. Once the Nanitor agent has been installed on an asset or a Nanitor collector has been configured to monitor it, Nanitor will automatically detect issues on your assets and collect them on the Nanitor server.
An issue can be detected on one or multiple assets but will be only listed once in the Nanitor issue list. A single occurrence of a detected issue on an asset is called an issue violation.
The assets on which an issue has been detected are visible on the issue detail page.
Issue priority
Each issue has a priority that is automatically assigned based on standardized external sources used by Nanitor. An issue has a separate priority rating (0-10) for each of three priority categories:
- Confidentiality refers to the risk of confidential information being leaked
- Integrity refers to the risk of data being corrupted or manipulated
- Availability refers to the risk of critical systems becoming unavailable
The overall issue priority, calculated as the highest of the three categories, determines what square an issue ends up in in the issue diamond (further details below).
Issue types
Issues are split into several issue types, representing different kinds of problems:
- Vulnerability issues are exploits in installed software or the operating system that hackers can leverage to get access to an asset or inject malicious software that can cause further damage to the IT infrastructure. A vulnerability is specified by a CVE number issued by the MITRE Corporation. CVE numbers are identifiers for common vulnerabilities and exposures. The severity of a vulnerability is defined by its CVSS (Common Vulnerability Scoring System) score, its presence in the CISA Known Exploited Vulnerabilities Catalog, and the likelihood of exposure defined by its EPSS (Exploit Prediction Scoring System) score. All three parameters are used by Nanitor to quantify the issue priority of a (CVE) vulnerability. Vulnerabilities are identified by the National Cybersecurity Federally Funded Research and Development Center and collected from the National Vulnerability Database (NVD). Vulnerabilities are often caused by missing software updates or patches.
- Misconfiguration issues are known insecure asset configurations as identified by benchmarks issued by the Center for Internet Security (CIS). Each benchmark consists of a rule set for an operating system (OS) and is considered the gold standard of how assets should be configured to ensure the greatest feasible resilience against attacks and to reduce the damage caused by breached assets. A benchmark is automatically assigned by Nanitor based on the OS of an asset. All detected benchmarks can be viewed from the security configurations view (Configurations -> Security configurations).
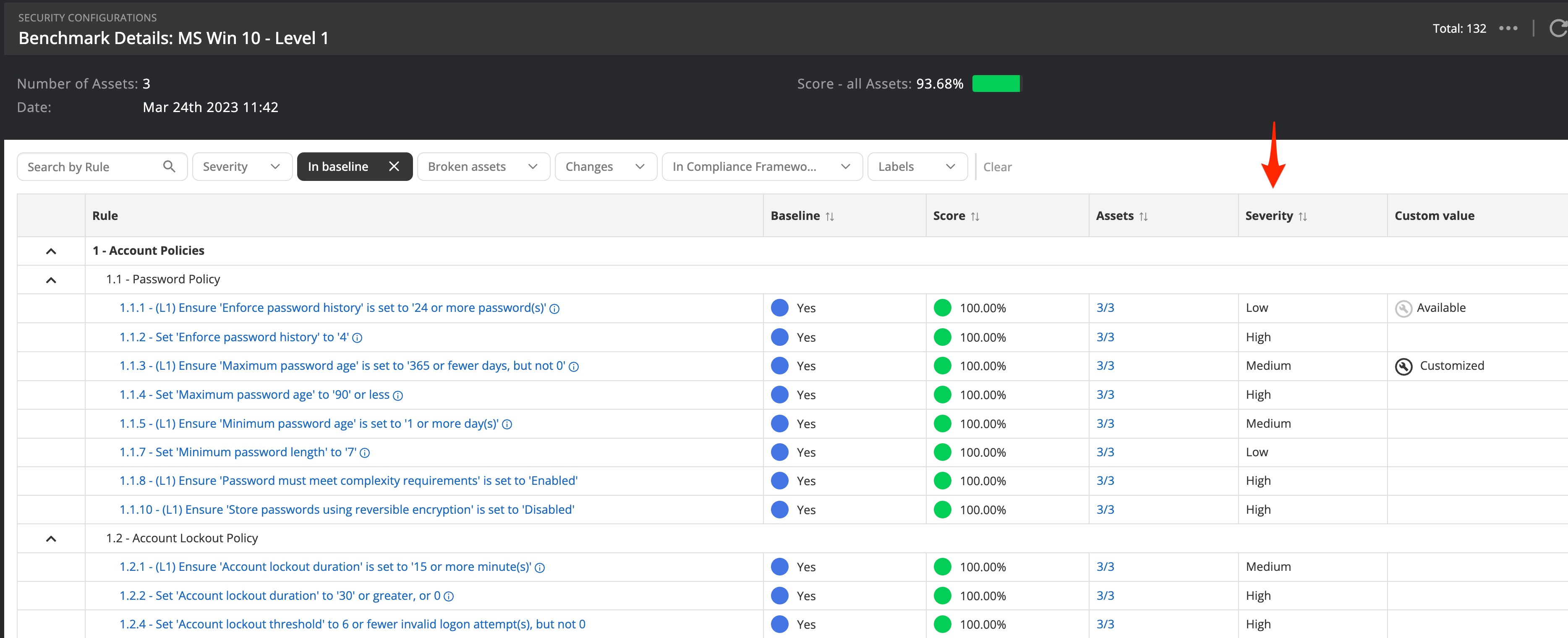
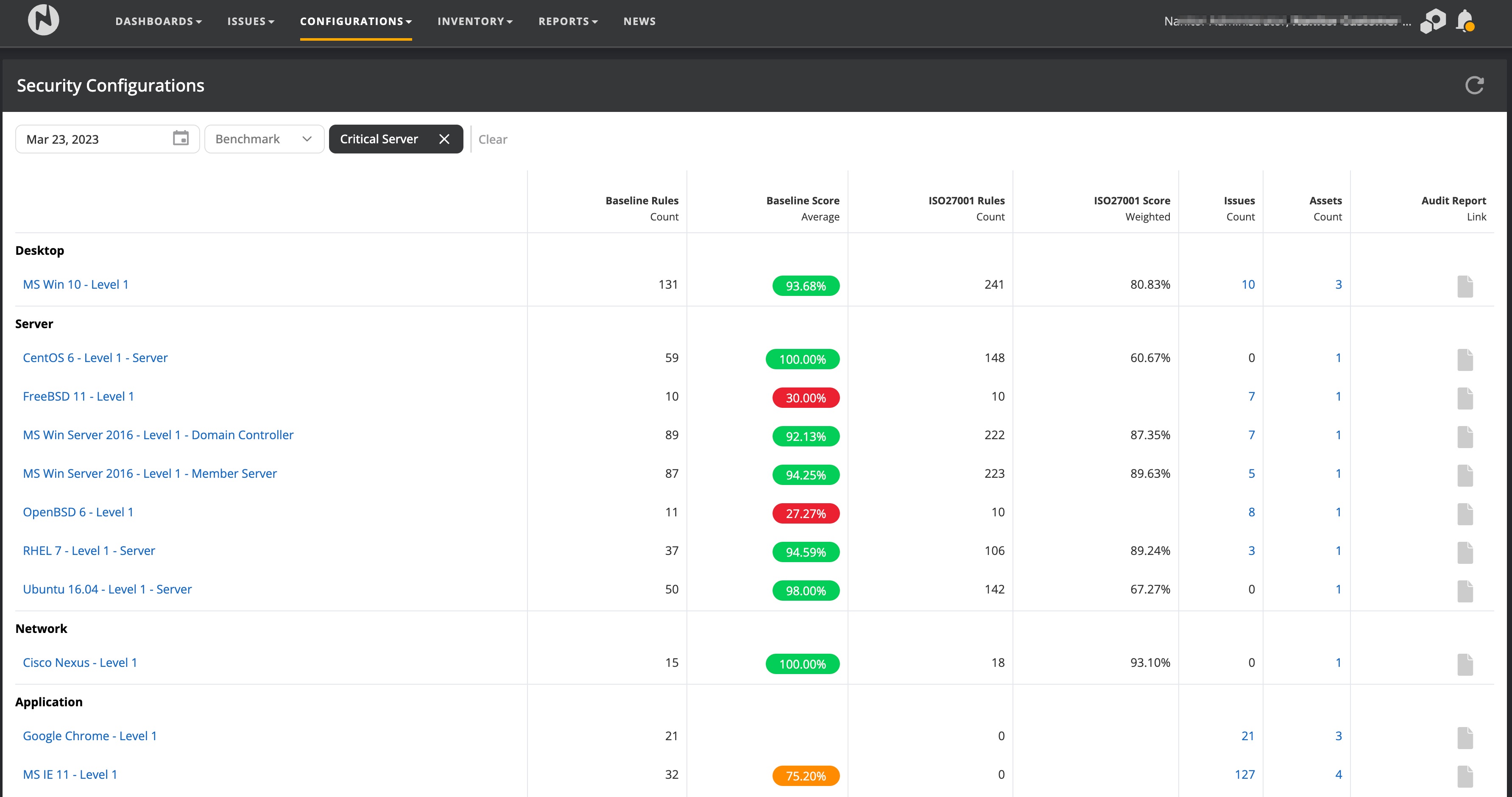 Opening a benchmark will reveal a list of benchmark rules according to the guidelines from CIS that Nanitor will check assets against. Nanitor adds severity to each benchmark rule based on recommendations by security experts. A severity of low will be given an issue priority of 1, medium 3, high 6, and critical 9.
Opening a benchmark will reveal a list of benchmark rules according to the guidelines from CIS that Nanitor will check assets against. Nanitor adds severity to each benchmark rule based on recommendations by security experts. A severity of low will be given an issue priority of 1, medium 3, high 6, and critical 9.
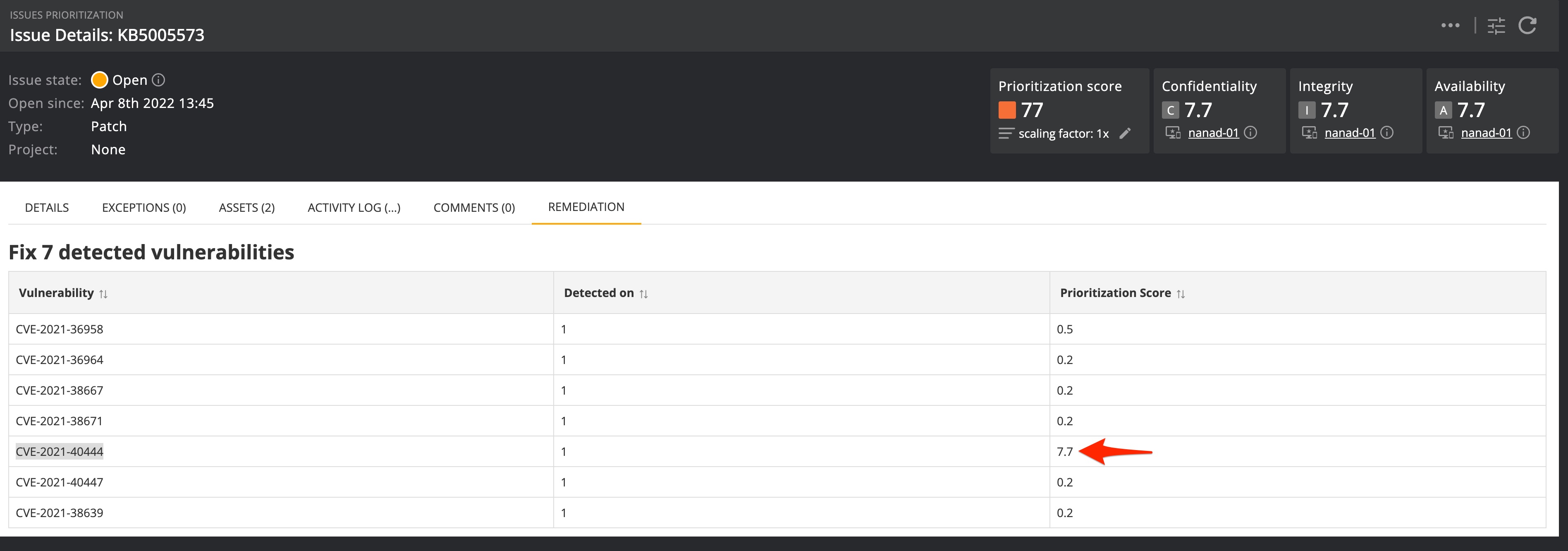
- Patch issues are patches that are missing on particular assets. Nanitor gets information on missing OS patches from the Nanitor agent installed on the asset. It makes a best effort to also identify which vulnerabilities a patch will resolve. Patch issues are given a default priority rating of 7 in each category, unless any of the vulnerabilities the patch resolves have a higher priority than 7 in that category, in which case the patch will receive the highest vulnerability priority.
- Software issues are raised when software found on the organization's assets has been blacklisted (or not whitelisted, if the 'strict' software policy has been enabled), or when software marked as mandatory is missing on an asset. By default, software issues are not flagged unless one or more Software detection rules are set.
- PII issues are personally identifiable information such as credit card numbers, social security numbers, or email addresses that have been discovered on an asset’s file system. The PII feature is disabled by default. It can be enabled and configured by administrators from the administration menu by navigating to Organization Management -> PII.
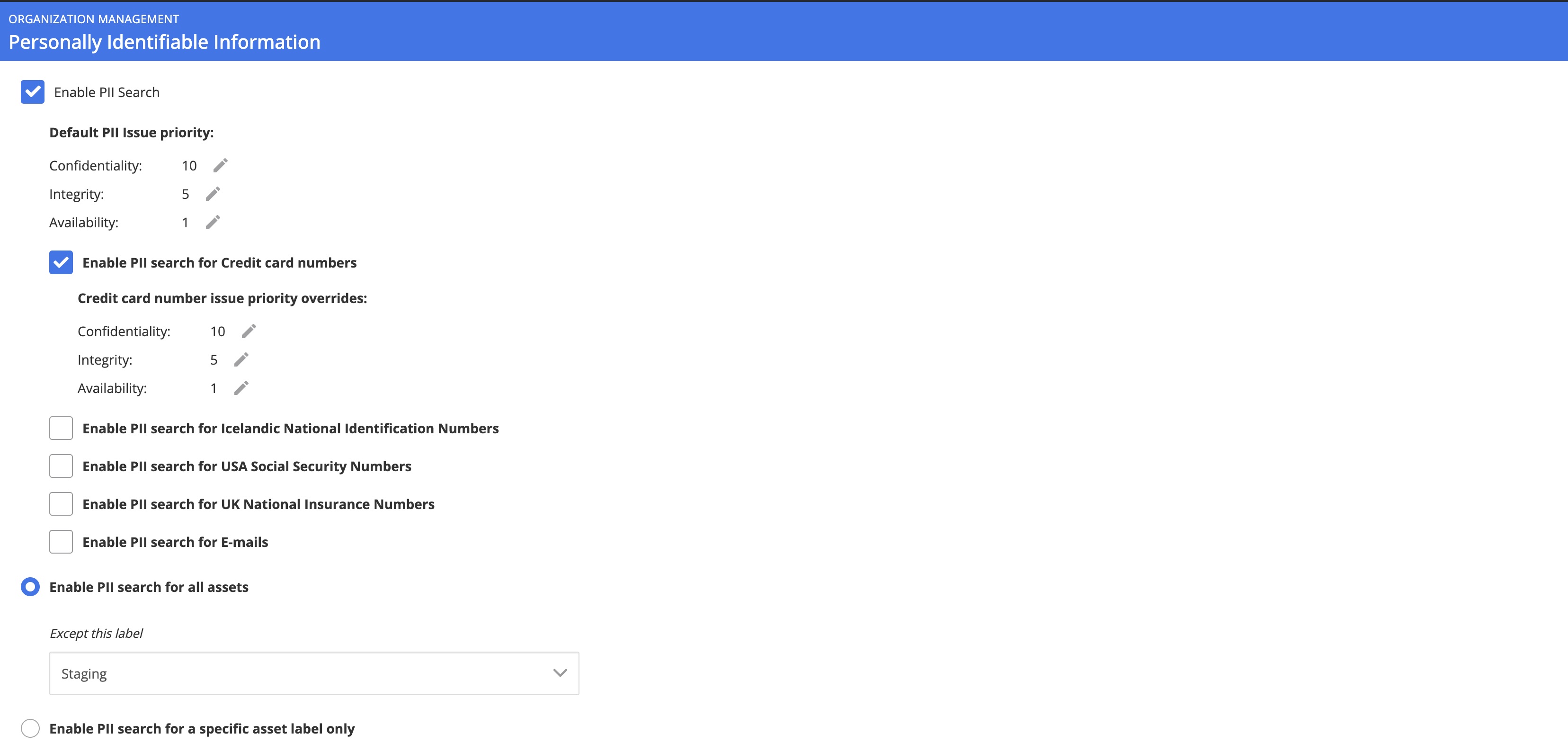 The PII search behavior (credit cards, social security numbers, emails) and the priority rating can be adjusted along with the ability to enable or disable this feature for certain asset labels only. As enabling PII search will add a lot of issues, it is recommended that this feature be rolled out for a limited set of assets only. The PII feature is currently limited to Windows OS based assets only. You can limit the number of possible PII matches by setting up a PII ignore list, for example, to restrict folder locations where PII should be searched for or whitelist dummy credit card numbers that appear in examples or documentation.
The PII search behavior (credit cards, social security numbers, emails) and the priority rating can be adjusted along with the ability to enable or disable this feature for certain asset labels only. As enabling PII search will add a lot of issues, it is recommended that this feature be rolled out for a limited set of assets only. The PII feature is currently limited to Windows OS based assets only. You can limit the number of possible PII matches by setting up a PII ignore list, for example, to restrict folder locations where PII should be searched for or whitelist dummy credit card numbers that appear in examples or documentation. - Device issues are problems with the presence of assets on the network or assets whose operating system is no longer supported (EOL).
Among this issue type might be assets that have been officially decommissioned but are still checking into Nanitor (indicating an asset may not have been properly reformatted and may still contain company data), assets discovered on the network that do not have a Nanitor agent installed and are not monitored by a Nanitor collector (if the network discovery feature has been enabled), or assets with blacklisted ports open (or non-whitelisted, if the ‘strict’ port whitelisting policy has been enabled).
What and how device issues are handled within Nanitor can be configured from Adminstration -> Organization Management -> Settings and then heading to the Device issues section in the Issues tab.
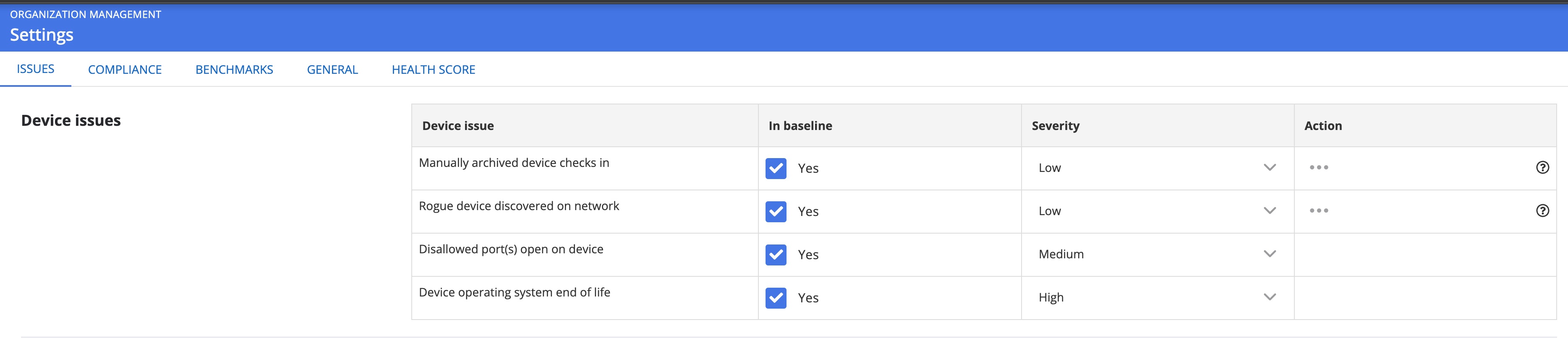 The selected severity determines the issue priority rating of these issue types.
The selected severity determines the issue priority rating of these issue types. - Identity issues are problems with identities that can access assets within the system, such as users with expired passwords, domain admins who can access non-domain controller assets, or users who are local admins on multiple different assets.
What and how user issues are handled within Nanitor can be configured by navigating to Adminstration -> Organization Management -> Settings and then heading to the User issues section in the Issues tab.
 The selected severity determines the issue priority rating of these issue types.
The selected severity determines the issue priority rating of these issue types.
Issue violations
An issue violation represents a specific instance of a violation on a particular asset, indicating the detection of an issue on that asset. By tracking issue violations, it is possible to gain deeper insights into the number and severity of issues affecting individual assets. The severity of an issue violation is defined by multiplying the asset priority and the issue priority and is a value between 0 and 100 where 100 represents the highest severity. The severity is expressed as the prioritization score in Nanitor which is explained below.
Understanding the number and severity of issue violations is crucial for prioritizing remediation efforts and managing security risks effectively. A large number of issue violations across multiple devices may represent a significant security concern, as each violation represents a possible entry point for an adversary. Therefore, organizations must allocate resources efficiently and reduce the likelihood of a breach or compromise by identifying the devices and assets that are most at risk. Instead of resolving an issue completely, it might be sufficient to resolve issue violations on the most critical assets by limiting the scope of remediation actions to the target set of assets. Scoping assets is done efficiently with labels defined on assets.
Overall, issue violations provide a more detailed level of granularity than simply tracking the creation or resolution of issues. By focusing on issue violations, security teams can gain a more comprehensive understanding of the specific instances of issues on individual devices and assets. This information is essential for effective security management and for reducing the likelihood of a security incident or breach.
Issue prioritization score
All assets have a priority rating similar to the issue priority rating explained above. The Nanitor Prioritization Score (NPS) for an issue on a given asset is calculated by multiplying together the priority ratings of the detected issue and the priority rating of the asset on the issue that has been detected. A prioritization score is calculated independently for each of the three categories (Confidentiality, Integrity, and Availability), with the highest of the resulting ratings treated as the overall Nanitor Prioritization Score for the issue on the asset. Since the asset priority might vary, Nanitor always considers the highest asset priority as the foundation for calculating the prioritization score for the issue as a whole. This allows the prioritization score to take into account how different issues might not have the same impact on every asset.
The Nanitor Prioritization Score is displayed as NPS to express that it is calculated based on the algorithm developed and maintained by Nanitor. The NPS is a value between 0 and 100 whereas 100 is the highest possible severity.
The higher the issue prioritization score, the more important it is to remediate the issue. The sum of the issue prioritization scores (adding the issue prioritization score of all affected assets) determines the impact for cybersecurity.
Nanitor classifies detected issues depending on the prioritization score.
- P0 issues have a prioritization score (NPS) between 81 and 100.
- P1 issues have an NPS between 64 and 80
- P2 issues have an NPS between 49 and 63