Security configurations
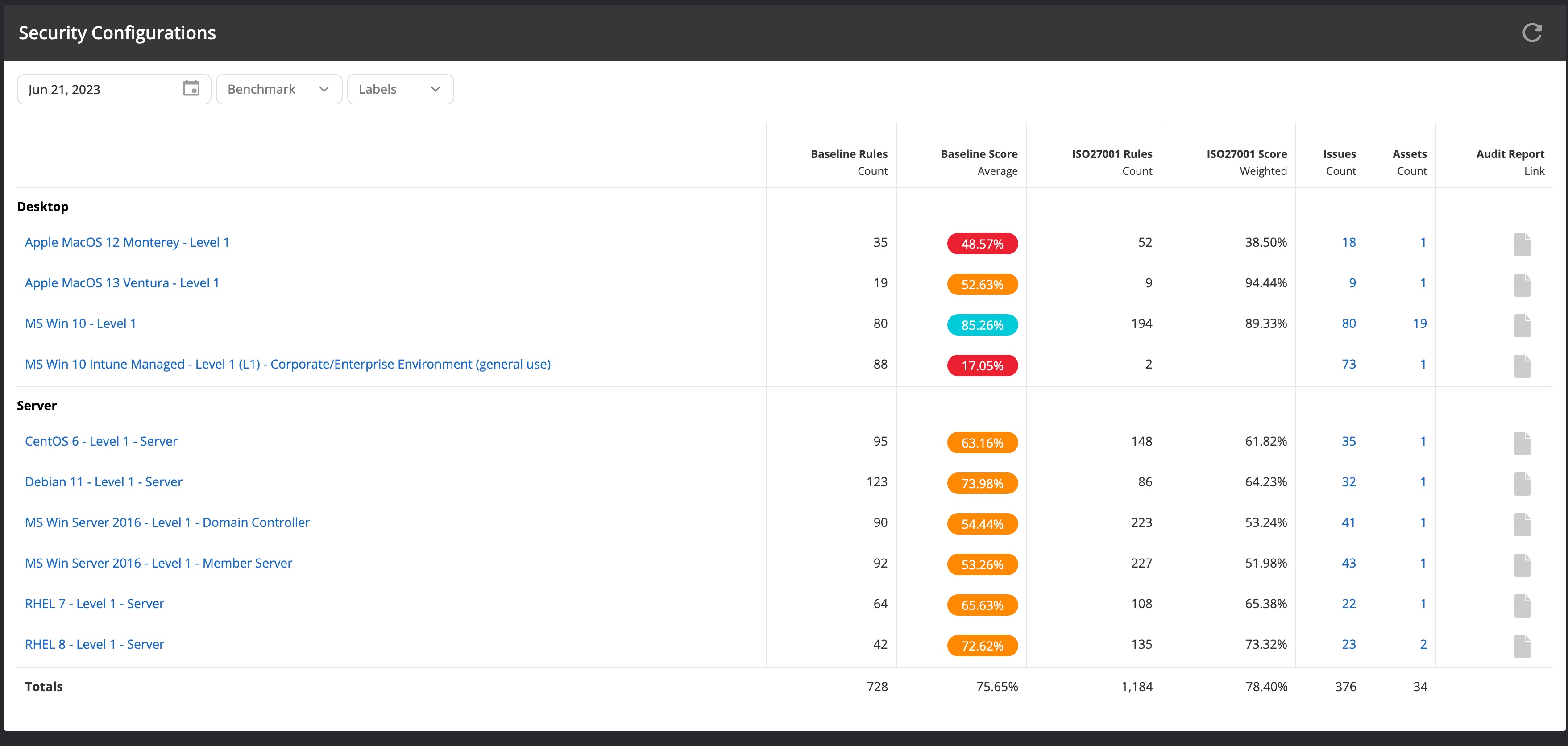
The security configurations report (Configurations → Security configurations) gathers information on all detected and supported CIS benchmarks across your IT infrastructure and the configuration status of your assets. The security configuration overview provides a quick view of benchmarks along with a color-coded score ranking the security configurations of the relevant assets.
The displayed report shows various columns:
| Field | Description |
|---|---|
| Baseline rules | Number of configuration checks from the benchmark that are in the baseline. A configuration check that is in the baseline will create an issue when the configuration check fails on any of the assigned assets. |
| Baseline score | The score of a benchmark is calculated from all passed and all available configuration checks in the baseline. |
| Compliance framework rules | This column shows the number of configuration checks that can be considered necessary for compliance requirements. Since you might have multiple framework checks enabled, Nanitor only displays the primary one. |
| Weighted compliance framework score | The score of the compliance framework is calculated from all passed and available configuration checks that have a match to a chapter in the compliance framework. The score is weighted by the severity of the configuration check. |
| Issues | The number of issues that have been created from configuration checks for this benchmark (an issue is created if a check is in baseline and is failing on at least one asset). |
| Assets | The number of assets that have been assigned to the benchmark. |
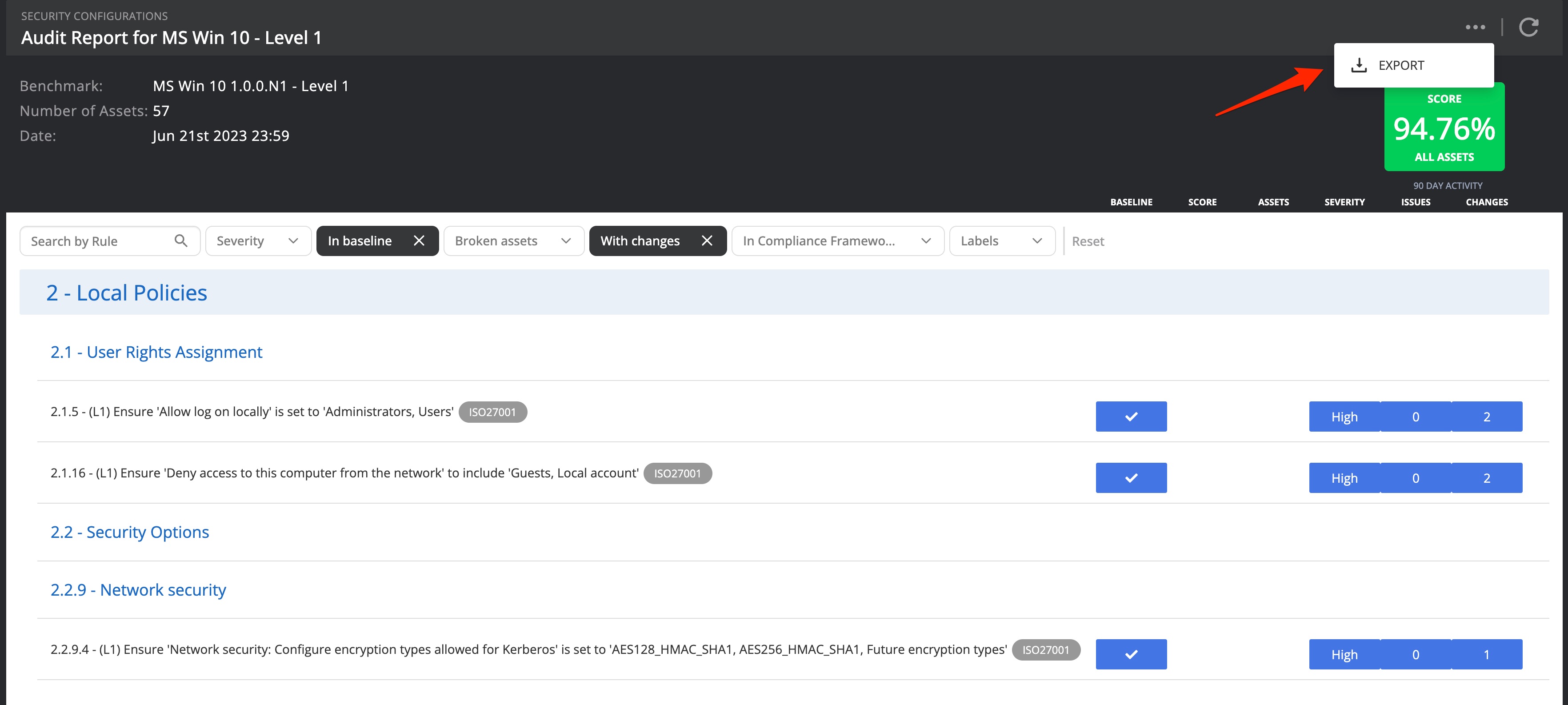
| Audit report | The audit report column links to a view (see screenshot below) that shows the benchmark in more detail. From there you can download the findings to a PDF report. |
From the security configurations front page you can click on any of the benchmarks, which will bring up more details on the benchmark itself and Nanitor's findings.
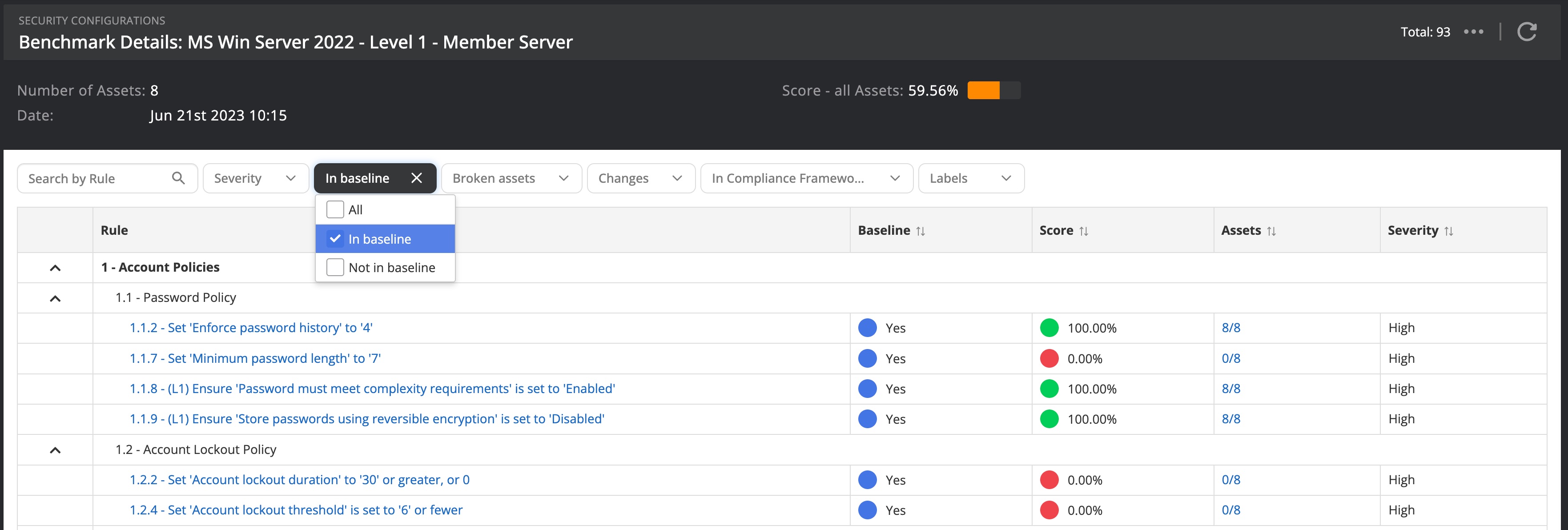
By default, the view is filtered on all benchmark rules that are included in the baseline. You can leverage other filter options to explore in more detail the security configurations that you are interested in:
- Severity of a configuration can be considered low, medium, high, or critical. The assessment of the severity is done by the security experts from Nanitor but can be overwritten.
- In baseline. The default view is to display only configurations that are considered meaningful to your organization's policy. You can look for configuration checks that are not considered (and therefore no issues will be created when Nanitor detects a misconfiguration) by applying the "Not in baseline" filter option.
- Broken assets refers to misconfiguration checks that are failing on at least one asset. It is possible to see only checks with broken assets, or only checks without broken assets.
- With changes refers to configurations checks where any changes have been applied, such as overriding severity or adding or removing from the baseline. For a more thorough overview of benchmark changes, refer to the Technical policy changes report available from the Reports menu.
- Compliance framework will filter configuration checks with a reference to a chapter in the chosen compliance framework.
- Labels will limit the assets affected to those with a certain label applied and adjust the score accordingly.
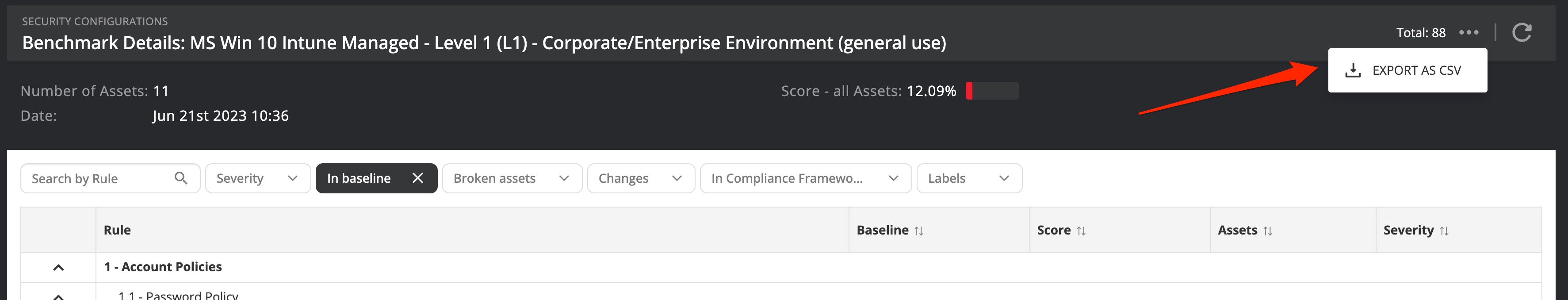
On the top right of the benchmark detail page, you can export the benchmark configuration checks to a CSV formatted file if you wish to work with the results from Nanitor in a spreadsheet application such as Excel.
The exported file includes the following columns:
| Field | Content |
|---|---|
| section | The section number as provided by Nanitor. This is not necessarily the same as the section number provided by the CIS benchmark. |
| title | The title of the configuration check as provided by Nanitor. This is not necessarily the same as what is provided by the CIS benchmark. |
| in_baseline | The baseline flag indicates whether an issue should be created in Nanitor when the configuration check fails. |
| severity | The severity as a number, where low=100, medium=200, high=300 and critical=400. |
| excluded | This flag will be true if all assets pass the configuration check, or if the created issue has been excluded completely (for all assets) by an exception. |
| num_broken | The number of assets where the configuration check is failing. |
| num_incidents | The number of separate times that an issue has been opened for this misconfiguration check. The "num_incidents" field is a legacy feature and will be removed in future releases of Nanitor. |
| num_changes | The number of times a change has been made to the technical policy for this rule, such as by removing it from baseline, putting it in baseline, or changing its severity. |
| org_frameworks | The compliance frameworks and specific chapters that the configuration check has been matched to. A configuration check can match multiple sections in a compliance framework. |