Onboarding
After your evaluation phase for a vulnerability management solution and your decision to go forward with Nanitor as the core tool to manage vulnerabilities on your assets, you need to establish a rollout plan that is aimed toward your expected outcomes and has realistic milestones defined. This guide helps you to plan the rollout of the Nanitor solution by providing a framework for you to follow to ensure a successful implementation. The framework includes important steps to be completed, in the correct order, within a defined timeframe, and resources to be present, available, and involved.
Outcomes
Before you get started the key goals to be achieved with the Nanitor solution need to be well defined. The goals (outcome) need to be achievable, within the feature range of the Nanitor solution, and timed. Nanitor is a third-party solution to increase cyber security resiliency for existing assets in your IT infrastructure. It is considered to be one tool out of many to minimize the overall risk of cyber security attacks and data breaches. When Nanitor is fully leveraged and anticipated within your organization it delivers among others the following core outcomes.
- For Nanitor to be able to provide the results expected it is essential to capture all assets in your IT infrastructure. Most of the assets are usually well known and easy to onboard into Nanitor. Enabling the recommended network discovery will reveal a long list of detected assets that need to be evaluated concerning their importance to cyber security. You will need need to make an assessment for the unknown assets, install clients for those assets where available, remove them from the IT infrastructure, or accept the risk of the existence of an unmonitored asset. This process can take a long time since you need to gather a lot of information and make conscious decisions. By the end of the asset-capturing process you have a complete overview of your asset fleet. Only a completely monitored list of assets will give you the confidence that you didn't miss anything. Nanitor is always on duty and captures newly detected unknown assets for monitored assets that
- Once all assets are captured you need to ensure to risk rate your assets. Only fully and accurately risk-rated assets ensure that the results presented by Nanitor are prioritized correctly. A prioritized list of detected issues is essential to focus on remediation of the issues that expose the most risk to your cyber security. A correct prioritizing of your assets will also ensure that the calculated results of your cyber security health are correct and represent reality.
- For each goal that you want to achieve there needs to be a report available that can capture the status of the key performance indicator that you want to capture as your goal to achieve. It might be the overall organizational security score but it can also be broken down by an issue type or a group of assets. But you can also define performance metrics for P0 issues only or issues that have any relevance to the compliance framework you need to work in accordance with. Or you might consider patching as the key to removing vulnerabilities and acting on those on time can be crucial. Nanitor provides many reports and dashboards for all kinds of use cases. Additionally, there is a public API available that can be leveraged to do all kinds of customized reports in third-party reporting tools like Power BI or similar. Reports with measurable key indicators need to be identified and defined at the beginning of the onboarding process since it affects the setup and configuration of Nanitor.
- Detecting and uncovering vulnerabilities is one thing but remediation of vulnerabilities is a completely different story. Nanitor is not a remediation tool but it helps by providing useful instructions and understanding the potential impact of a vulnerability. Nanitor provides comprehensive remediation instructions but what remains is the actual removal of a detected vulnerability on your asset(s). Alternatively, you may accept the risk of a vulnerability by doing an exception for the issue partially or for your entire asset fleet. Understanding the resources and effort needed to do the due diligence of detected issues and remediate those is key to improving your IT security overall. Without the resources and their efforts the security level of your IT infrastructure will stay the same.
- Understand the tracking capabilities in Nanitor and understand the difference between the core features of Nanitor (configurations, vulnerabilities, patches, and user privileges) and other additional features (software blacklisting, network discovery, PII)
Resources
Implementing Nanitor requires resources. The areas of responsibility span installing Nanitor clients, maintaining and follow-up on detected issues in Nanitor, or decision-making for implementing and applying technical policies. For a successful roll-out that ensures the desired outcome gets defined and reached it is essential to announce a product champion of the Nanitor platform that provides tailored training needs to stakeholders, facilitates meetings with stakeholders, and ensures necessary decisions are made and follows-up on agreed action items.
Nanitor acts as the single source of truth concerning cyber security threats to your assets. Detected results need to be reflected and verified at all times. Additionally, you need to verify the health of the Nanitor clients. That is to ensure:
- All assets are captured, are reporting into Nanitor as intended, get a benchmark assigned, have an up-to-date agent, and are risk rated
- Decide on how to continue with discovered rogue devices
- Decide on how to proceed with assets where the operating system is end-of-life (EOL)
- Adjust the assigned baselines according to the technical policy and reflect the importance of the assets. If needed assign new, more or less strict benchmarks to a subset of assets that require a more secure, hardened operating system that needs to comply with higher security standards
- Review results of existing and newly detected vulnerabilities. Assign detected issues to remediation projects to keep track of progress and assign ownership.
- Review installed software titles and tackle software titles to be removed or software that needs to be installed
- Patching is performed and results in Nanitor are in accordance with patches installed by the patching teams
All of the tasks above require resources. Not only to perform those tasks but also to organize meetings, facilitating those by tracking and follow-up on agreed action items. You will also find yourself in a situation where responsibilities for certain areas are undefined or unclear, and finding the responsible people and involving them will take time and might cause a delay in any of your rollout plans.
The customer lifecycle
Onboarding and adopting Nanitor may not essentially start with the purchase of a license. Ideally, you have already installed a trial version and have a good understanding of Nanitor's capabilities, and are familiar with the insights you gathered from your IT infrastructure by installing a limited number of assets. However, it is important to have a plan in place that you can refer to and guide you to a successful usage of Nanitor that helps to increase transparency and the resilience of your cyber security landscape by providing measurable KPIs.
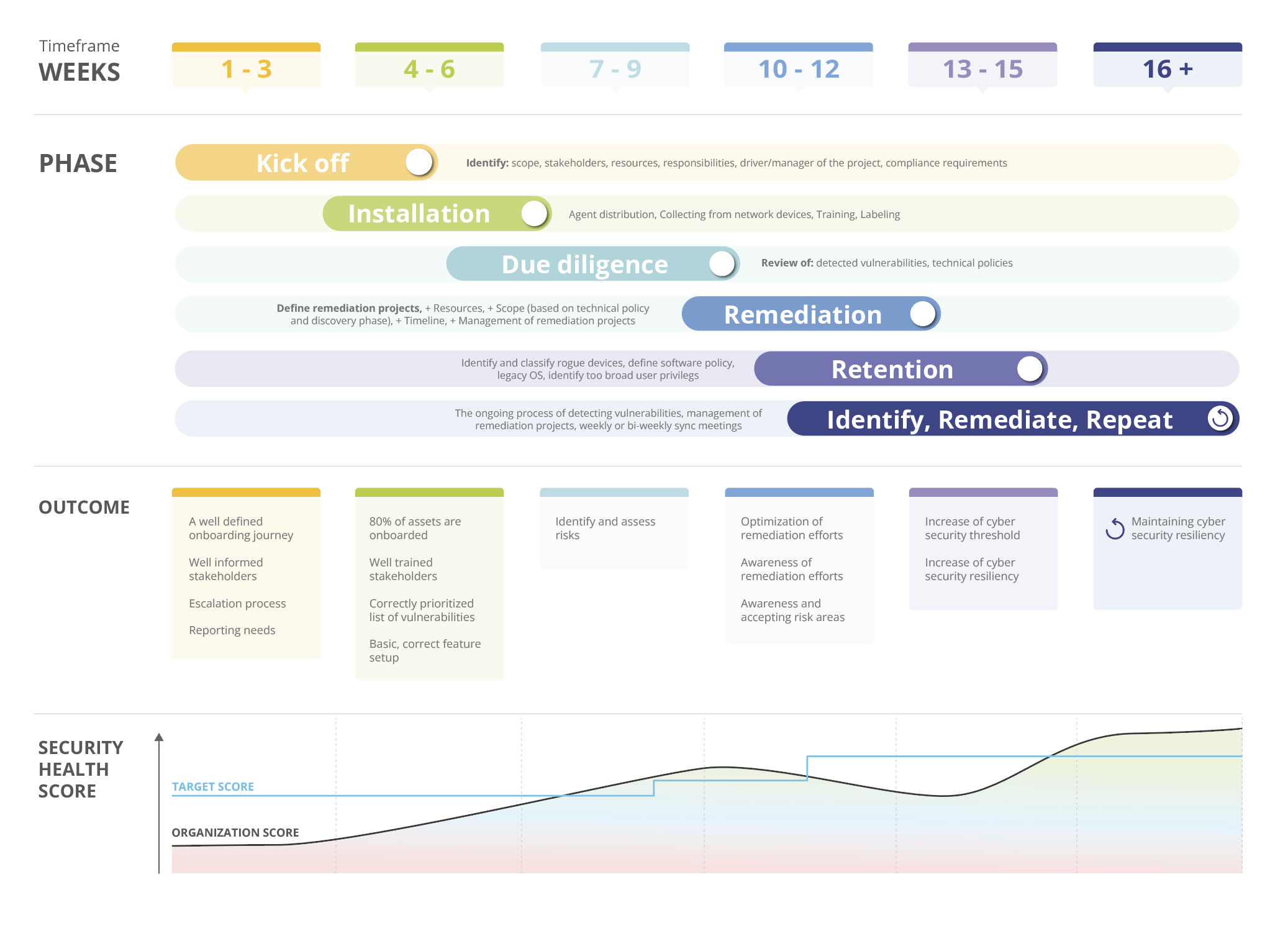
During the Nanitor journey from Onboarding to adoption and to retention you should be aware of what are deliverables within each lifecycle phase. The image below illustrates the phases with time estimation. Based on the outcomes to be achieved in each phase and the resources to be involved in the cyber security program each phase can be longer or shorter and should serve as an orientation to define timely scoped milestones.
The lifecycle stages can be considered and scoped as follows:
Kickoff
The kickoff defines the overall outcomes to be achieved and lays out the roadmap
- Kickoff meeting where to:
- Agree on the scope
- Identify stakeholders
- Identify resources
- Identify the driver (product champion) of the Nanitor rollout
- Define and agree on desired outcomes
- Reports to be delivered
Installation
- Distribution of the Nanitor agents
- Installation or configuration of the Nanitor collector if required
- Priority rating (criticality) of assets
- Labelling of assets using automatic rules
- Basic training on Nanitor for stakeholders
Due diligence
- Due diligence on detected issues
- Vulnerabilities
- Misconfigurations
- Patch status
- User privileges
- EOL devices
- Software inventory
- Identify resources
Remediation
- Start technical policy review (benchmarks)
- Define remediation projects
- Resources
- Scope (based on technical policy and discovery phase)
- Timeline
- Management of remediation projects
- Establish weekly or bi-weekly sync meetings
- Identify resources bottlenecks or lack of resources
- identify risk
Retention
The final onboarding tweak is sometimes considered a low priority but far from less important. To leverage all of Nanitor's capabilities and ensure better retention it is important to pay attention to a couple of items:
- Reporting
- Reporting to senior management on progress and achievements
- Identify gaps in reporting
- Reporting to/in 3rd party applications by leveraging available API endpoints
- Collaboration
- Inform involved teams by setting up email notification rules and/or a Slack channel for quicker response times on upcoming/newly detected issues in crucial areas of your IT environment
- Integrate with your ticketing systems / service desks (such as Jira) where your IT teams and experts work with daily
- Identify rogue assets
- Nanitor agent installation on missing assets
- Verifying known rogue assets
- Spot inactive assets
- Review software inventory
- Mark unwanted software
- Mark mandatory software
- Review user policy
- Remove unnecessary user privileges
Identity, Remediate, Repeat
After the initial onboarding process, you should be able to return to repeating cycling mode where you continuously identify and remediate newly detected vulnerabilities and maintain the achieved IT cyber security resilience level. Fading into this phase means you have managed to onboard all your assets to watch for, have successfully managed to involve necessary resources, and are sufficient in using Nanitor, and you have done the final touches in adjusting the settings in Nanitor. You should also have all reports in place for upper management to report on the overall security level and for the stakeholders to report on progress on agreed remediation projects and to identify vulnerabilities that need remediation.
- Weekly/Bi-weekly sync sessions
- Decide on newly detected vulnerabilities either by remediation or by excluding issues temporarily or forever.
- Track progress and adjust remediation projects
- Create new remediation projects if resources are available or demand those
- Compliance reporting
- Security metrics reporting
- Other reporting to see if security KPIs are met
- Decide and agree on improvements
The cyber security landscape is never ending and new vulnerabilities are discovered all the time. Requirements are adjusted that need to be reflected and new operating systems are adopted that are in most cases more or less insecure by default. Software and operating systems are becoming out of support from the maintainer or issuer. Having that in mind an ongoing, recurring process in place is essential that you keep up with IT security threats. Nanitor supports you in that process to improve your IT security, ensure to keep the desired level, and focus on vulnerabilities that have the greatest impact on your IT infrastructure which ensures an effective and efficient usage of your IT security resources.