Assets overview
An asset (or a device) is an information system (e.g., a Windows laptop, a Linux server, a SQL database, etc.) that contains data and can be interfaced typically both through the network or locally.
Assets are fundamental to organization security, as they typically have access to data and information, and they are all connected within an organization through networks and domains.
Asset discovery
The asset is created and updated based on information provided by an information source during asset discovery. Assets can be discovered by the following means:
-
Active Directory discovery: Assets that are a part of the Active Directory domain. The discovered assets are not monitored and have the Authorized status. The Active Directory asset discovery can be enabled in the Organization management.
-
Agent: An agent is installed on the asset and is reporting information to the Nanitor server. The asset is being monitored. Nanitor agent installing instructions
-
API: An asset is added via API. The asset is not monitored and has the Authorized status.
-
Collector: A collector connects to the asset, fetches information and then sends it to the Nanitor server. The asset is being monitored. Nanitor collector installing instructions
-
CSV: The information about the asset has been provided manually through CSV file upload to track the presence of the asset. The asset is not monitored and has the Authorized status.
-
DHCP: An asset is added via API and marked as DHCP. The asset is not monitored and has the Authorized status.
-
External asset discovery: External assets are devices identified via external scans, visible from outside your organization’s network. Their details and internal health status are not fully known until further examination. These assets could be accessible or vulnerable to external entities. See the External asset discovery chapter for more details. The external assets can have two levels of visibility: External (the device relies only on external sources for gaining information) and 360° Visibility (information about the device state is received both from the external sources and via Nanitor Agent or Collector).
-
Manual: The information about the asset has been provided manually. The asset is not monitored and has the Authorized status.
-
Network discovery: Assets seen on networks reported by other agents through ARP tables. network discovery can be enabled on a per-network basis. Discovered assets are reported as Rogue assets and are not being monitored. Each entry includes IP and hardware addresses of an asset. Network enabling instructions.
-
Parent asset: An asset is collected via its parent asset. For example, a VMware Esxi asset discovered via the VMware Control Center. The asset is monitored by the parent asset’s collector.
Asset states
An asset can have one of the following states:
- Active: The asset is actively reporting to Nanitor.
- Inactive: The asset has not reported into Nanitor for over a specified threshold. It’s 24 hours if it’s an asset with an agent, or 36 hours if it’s a collected asset.
- Authorized: The asset is not being monitored by Nanitor, but has been authorized and is now considered a legitimate part of the network.
- Rogue: The asset was discovered by Nanitor's network discovery mechanism and is not in active monitoring by Nanitor. This device might be an unauthorized one sniffing the network and serving as a proxy for adversaries. At the same time, it might also be a legitimate device that simply hasn't been set up for monitoring, or it may not be supported for data collection.
- Pending archival confirmation: The asset is of a type that is set to be manually archived and has passed the threshold for being archived but requires manual confirmation.
- Archived: This asset has been archived and is no longer being tracked by Nanitor.
To ensure network security and integrity, it is strongly recommended to identify rogue devices and determine their authorization status on the network. If a rogue device is unauthorized, immediate action should be taken to block its access to the network, investigate any potential security breaches, and mitigate any damage. If the device is legitimate but not set up for monitoring, appropriate measures such as installing an agent or setting up a collector should be taken to ensure proper monitoring and timely detection of security issues.
Overall, identifying and verifying the status of the device is crucial in determining the appropriate course of action to maintain the security of the network.
Asset state graph
The graph below shows how an asset can move between the different states.
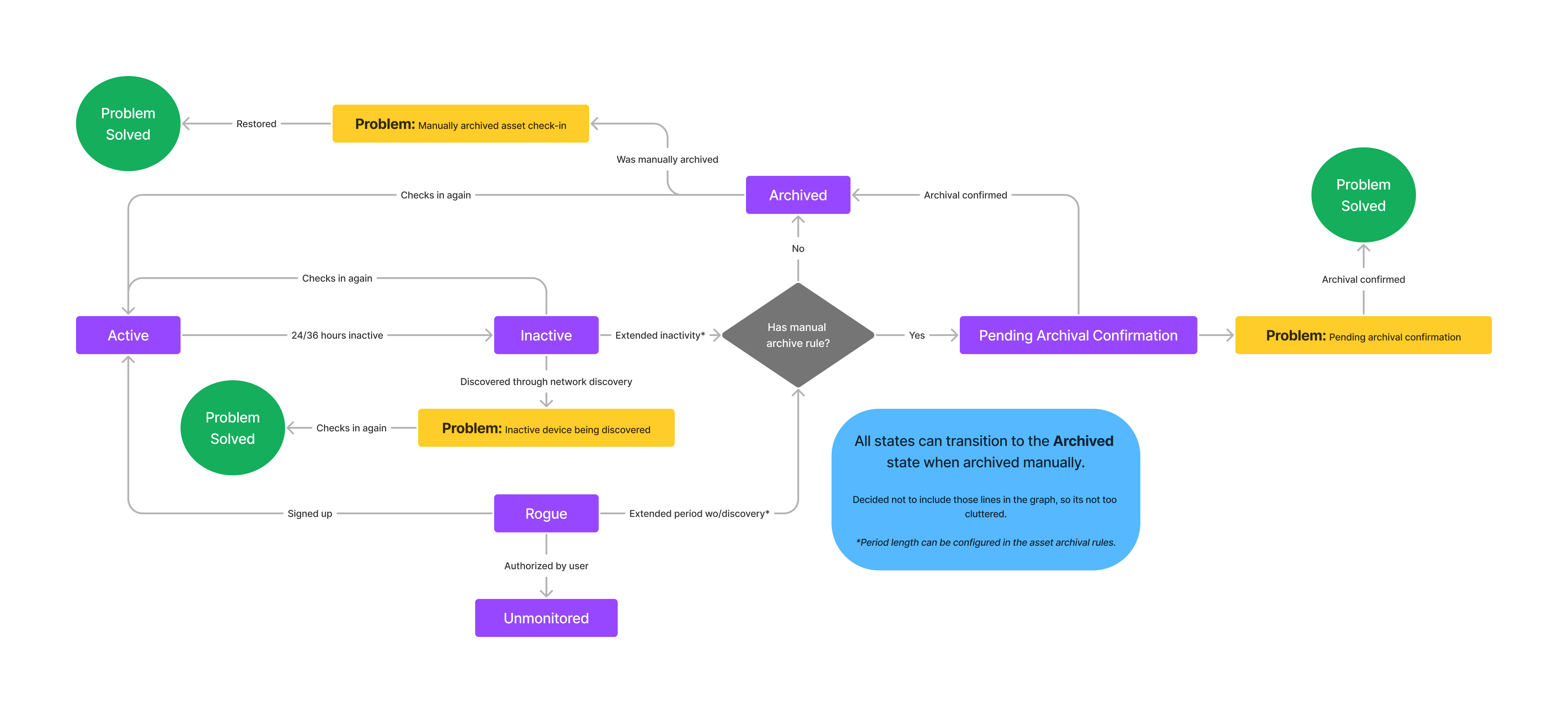
Asset activity problems
In addition to the asset states an asset can also have some activity problems, depending on how it moved between the different states. These indicate that there is something problematic with the assets state and that some action may be required. These problems are:
- Manually archived device checking in
- This asset was manually archived but is still actively checking into Nanitor. This indicates the device has not been properly reformatted and may contain other company data.
- Remediation: Remove the Nanitor agent from the machine, or restore the device if it is still in use.
- Inactive asset is being discovered
- This asset has stopped checking in, but other assets are still discovering it on the network. This could indicate a problem with the agent or collector.
- Remediation: Check if the agent is running on the asset or if its collector is unable to connect to it.
- Asset is pending archival confirmation
- This asset has passed the threshold for being archived but requires confirmation.
- Remediation: Confirm the archival in the UI (or fix the assets agent/collector so it starts checking in again.)
Asset state graph with activity problems
The graph below shows how an asset can move between the different states.
Asset priorities
Asset priority is defined in terms of confidentiality (C), integrity (I) and availability (A), on the scale of 1 - 10. While the user may decide on their own asset priority ranking, we recommend the following ranking criteria:
The ranking guidelines are available in the product also while performing priority ratings.
The asset priority will impact how issues found on the asset are prioritized which is used in remediation and deciding what issues to prioritize for remediation. Learn more about prioritization in our Prioritization article.
The priority can be assigned through several means:
- Directly on the asset in the Asset Detail.
- Through asset labels, where an asset priority can be defined on the label and applies to assets having the label.
- Through benchmarks.
Asset labels
Asset labels are used to track groups of devices, for example:
- Services
- Teams
- Technologies (E.g. Windows / Apple, etc.)
- Public IP
New labels are created under Administration -> Organization management -> Labels.
Furthermore, automatic label assignment rules can be created for each label. They can for example be based on platform, IP, etc. See more about that under Administration documentation.
Please note that if your organization is a suborganization, then labels and automatic label assignment rules can be inherited from the parent organization if defined as inheritable. You can use them or create new ones. Labels inherited from the parent organization have pink background whereas organization's own labels have blue background.
Asset types
The asset type specifies what type of device the asset represents. This is an important property for asset management and reporting.
Asset type is automatically assigned to assets based on information from the system or specified when setting up. It can be one of:
- Laptop: A portable laptop. This is typically reported by the operating system.
- Desktop: A desktop computer or user workstation.
- Database: A database that is being collected from.
- Cloud: Cloud services, e.g. AWS EKS, Microsoft Office 365, etc.
- Cloud image: A docker image that is used in a running Kubernetes service.
- Kubernetes Cluster: A Kubernetes cluster imported via API. See Kubernetes Inventory and Vulnerability Scanning for details.
- Kubernetes Workload: A Kubernetes Deployment, StatefulSet, or DaemonSet imported via API. Workloads are linked to their parent Cluster and can have vulnerability data with package-level details.
- Server: A server computer or a domain controller.
- Network: A network device.
- Rogue: Rogue devices found through network discovery get a rogue device type. See more detail in the section above on the Rogue asset state.
Platforms
Nanitor supports a wide range of platforms that is growing continuously. The key platforms supported include:
- Microsoft (Windows)
- Linux (RedHat, Debian, CentOS, Ubuntu, and many other distributions)
- Apple MacOS
- Cisco IOS, ASA, NXOS network devices switches and routers.
- JunOS network devices
- Many other types of network devices, clouds and applications.
The full extensive list can be found on our KB page: Knowledgebase - Benchmarks and platforms.
Checks
To identify security issues, multiple checks are performed on an asset. The Nanitor discovery engine currently supports checks of the following issue types:
- Security misconfigurations are identified in Benchmarks where the system configuration is benchmarked against best practice guidelines from CIS, vendor guidelines, and our own. Benchmarks are groups of checks for security misconfigurations.
- Missing security patch that needs to be installed.
- Vulnerability in the operating system or installed software. Vulnerability checks identify vulnerabilities applicable to the device.
- In-compliant software, i.e. software installed on the machine that is either blacklisted or not whitelisted, or mandatory software that is missing.
- Personally identifiable information (pii).
Note that assets don't always support all the check mechanisms.



