Issue Details page
A detected issue has many aspects that need consideration. Nanitor helps you mitigate potential security risks both by prioritizing issues and by providing the necessary context needed to understand the issue and do due diligence. Nanitor keeps track of the complete history of the issue, and comments can be added on a given issue to pass information to other stakeholders.
Header
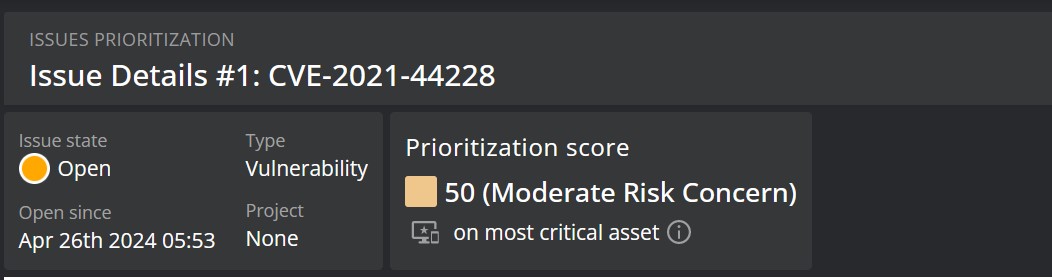
In the header of the issue detail view, you will get basic information about the detected issue, such as:
| Property | Description | Options |
|---|---|---|
| State | Issue state | Open, Closed, Excluded |
| Open since | Date and time since the issue was last discovered | |
| Issue type | The category the issue falls into | Vulnerability, Misconfiguration, Patch, Identity, Software, PII, or Device |
| Project | The remediation project(s) an issue has been assigned to | |
| Prioritization score | The issue's Nanitor Prioritization Score (NPS). | Critical Impact Threat, High Urgency risk, and Moderate Risk Concern |
| Most critical asset priority | Click the information icon near the label to see a tooltip showing which assets on which the issue has been detected have the highest confidentiality (C), integrity (I) and availability (A) scores. These values are used in the calculation of the issue's NPS. |
Overview tab
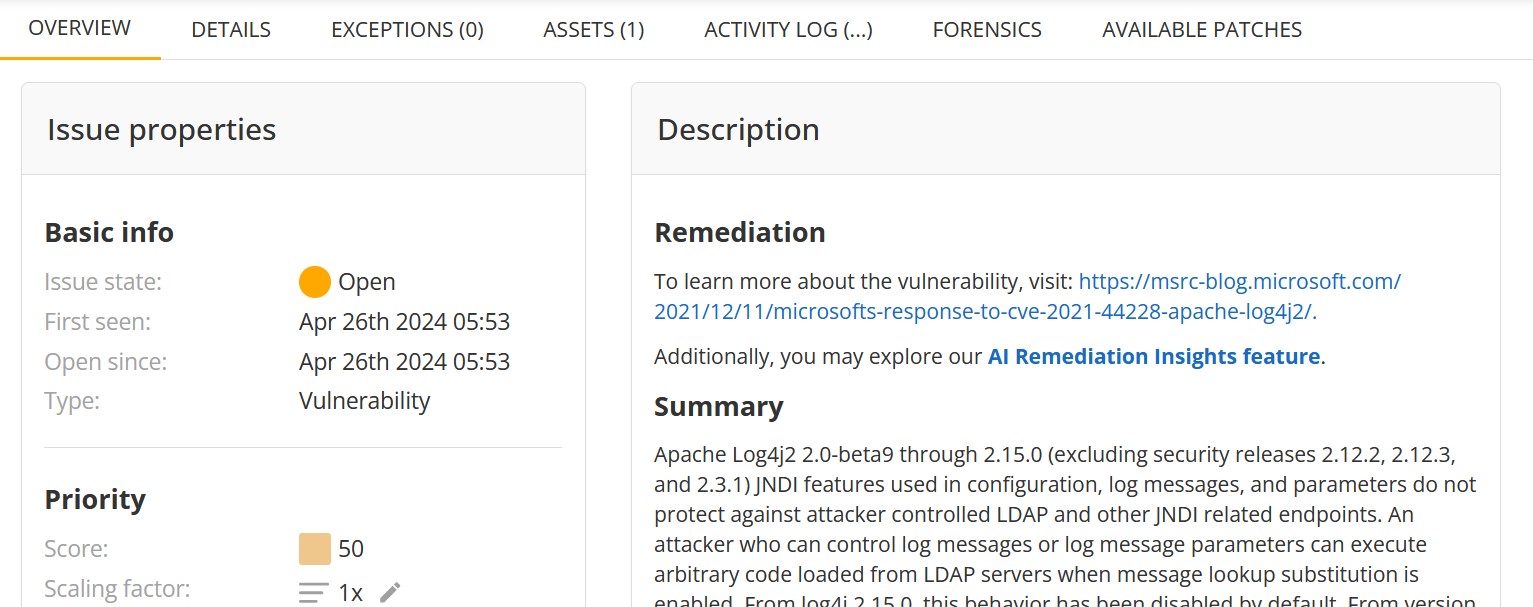
The Overview tab contains the main information regarding an issue. For more detailed information, open the corresponding tab.
The Overview tab contains the following sections:
- Issue properties:
- Basic info: The issue state, open since date and time, first seen date and time, and issue type.
- Priority: The issue prioritization score, priority scaling factor and issue priority in terms of confidentiality (C), integrity (I) and availability (A). By default, each issue has a priority scaling factor of 1. The scaling factor is an indicator of how important you rate a specific type of detected issue. The priority scaling factor can be overwritten for a single issue if needed or desired.
- Jira: A link to the ticket in Jira, if available.
- Health score impact: Information on how fixing the issue will impact the organization's overall health and health for the specific issue type (for example, vulnerability health or identity health).
- External / Industry standards: For some types of issues, such as Vulnerability issues, this section displays information on whether the issue belongs to the [CISA Known Exploited Vulnerabilities Catalog] (https://www.cisa.gov/known-exploited-vulnerabilities-catalog) and is considered ransomware, as well as its EPSS score and CVSS vectors. It also includes the list of compliance frameworks affected by this issue.
- Project: The list of projects to which the issue is assigned.
- Issue description: Short issue description.
- Assets affected: General information on the number of assets affected by the issue, as well as OS and labels of these assets.
- AI remediation insights: AI-powered suggestions for remediating the detected issue. See AI Remediation Insights below for details.
- Comments: Comments, if any.
Inventory lists
The inventory lists provide detailed information about the inventory related to the issue. Each list is accessible by clicking on the corresponding tab. The information included in each inventory list is documented below.
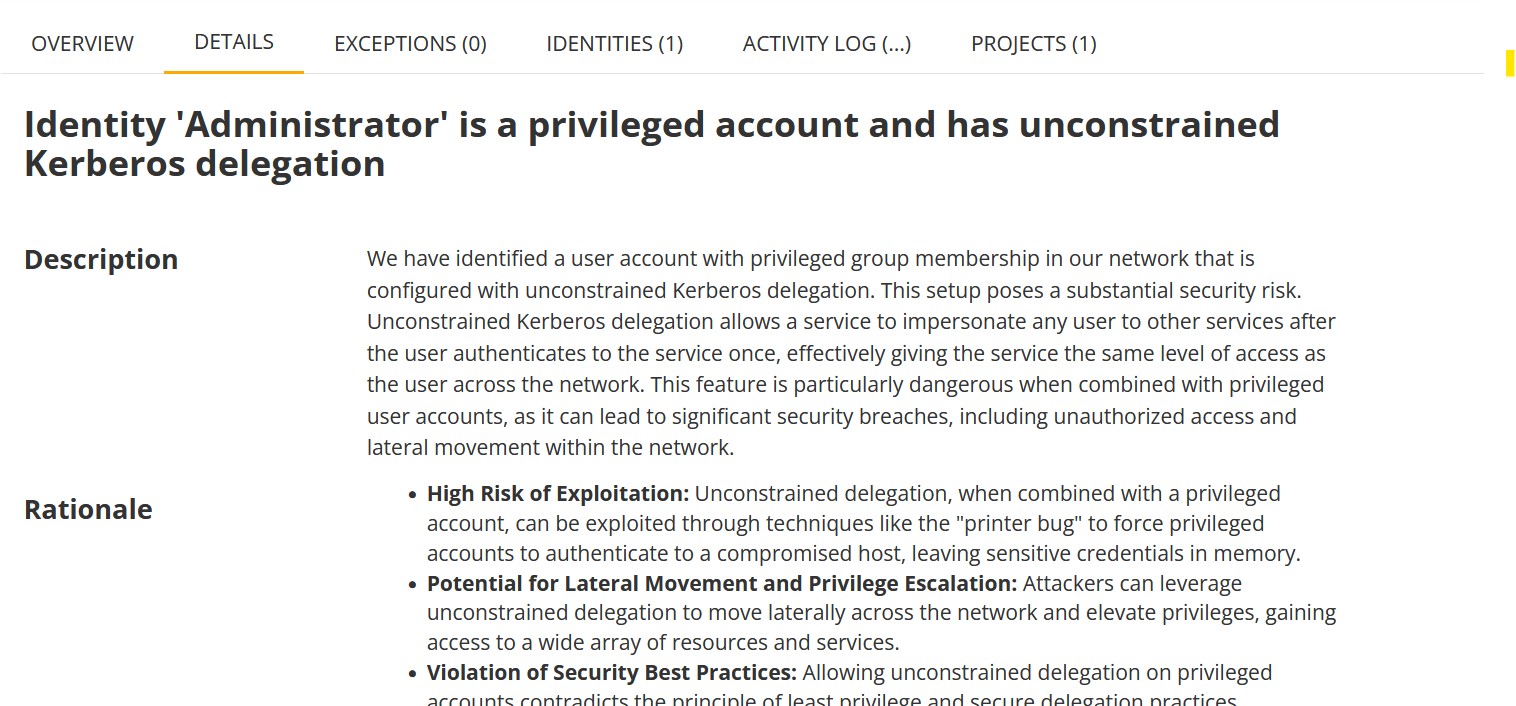
Details
This tab displays details on the detected issue including its technical details, external links, if any, and remediation suggestions.
Exceptions
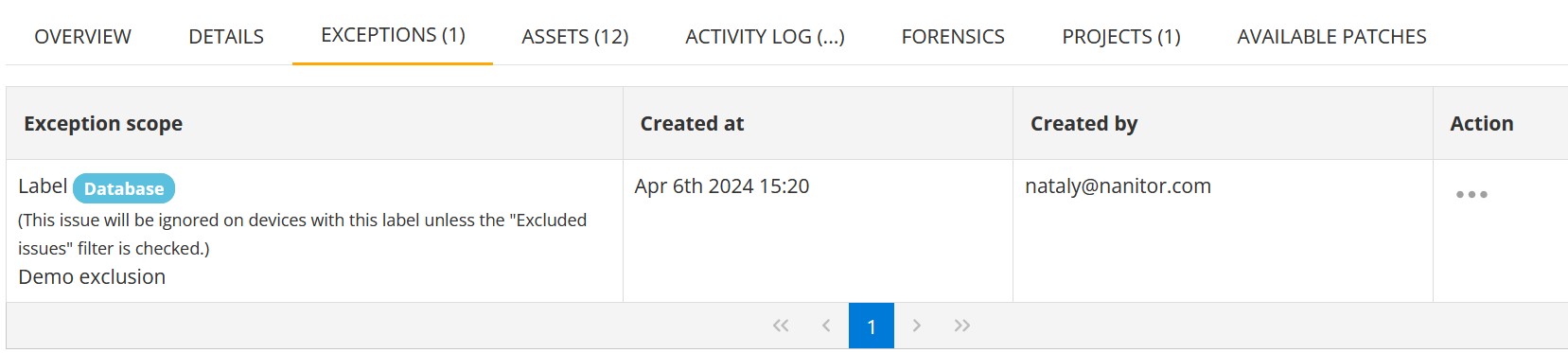
The Exceptions tab lists the exclusions made for the issue. This table includes the following columns for each exception in the list:
| Column | Description |
|---|---|
| Exception scope | The labels of the assets on which the issue will be ignored. It also contains the explanation provided when the exception was created. |
| Created at | The date and time of the exception creation. |
| Created by | The nanitor user who has created the exception. |
| Action | Possibility to remove the exception. |
Forensics
This tab provides further information helpful for remediation purposes to identify exactly what Nanitor has detected and where. For vulnerabilities, the forensics tab is grouped by assets where the vulnerability has the same root cause. For Identity issues, the forensics tab provides information on the UI location of the detected issues for easier remediation
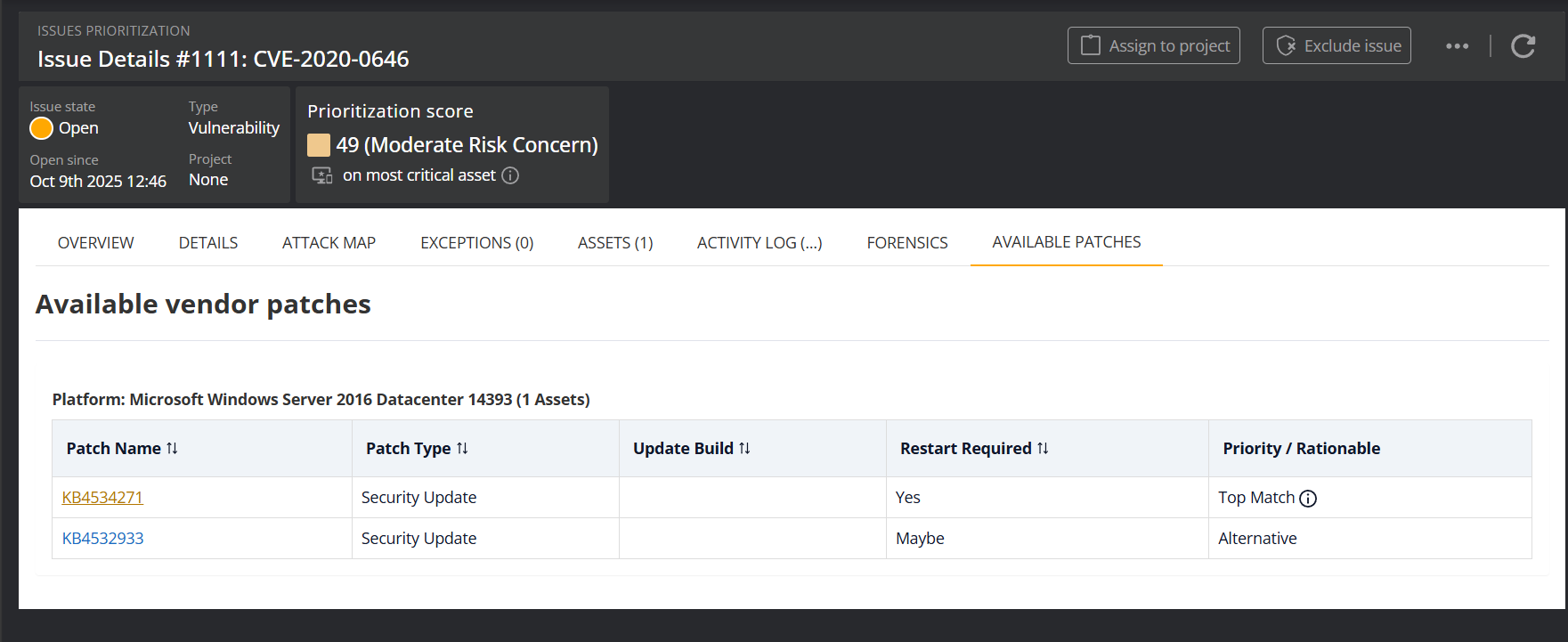
Available Patches
For vulnerability issues affecting Windows systems, the Available Patches tab provides detailed guidance on available vendor patches. Patches are grouped by the specific operating system version (e.g., "Microsoft Windows Server 2016 Datacenter 14393") to ensure you see only relevant patches for the assets in your environment.
The table displays the following information for each patch:
| Column | Description |
|---|---|
| Patch Name | The KB article number, linked to Microsoft's documentation |
| Patch Type | The type of update (e.g., Security Update, Security Hotpatch, Cumulative Update) |
| Update Build | The Windows build number after applying this patch |
| Restart Required | Whether a system restart is needed (Yes, No, or Maybe) |
| Priority / Rationale | Indicates the recommended patch with "Top Match" label |
Top Match Prioritization
The "Top Match" label indicates the recommended patch for each OS group. Hover over the info icon to see the prioritization rationale, which considers:
- Supersedence: Newer patches that replace older ones are prioritized
- Patch Type: More comprehensive patch types are preferred (e.g., Hotpatch > Cumulative Update > Security Only)
- KB Number: As a tie-breaker, patches with higher numbers are selected
This automated recommendation is based on public vendor data. Always consider your organization's specific testing and deployment policies before applying updates.
Inventory lists
The inventory lists provide detailed information about the inventory related to the issue. Each list is accessible by clicking on the corresponding tab.
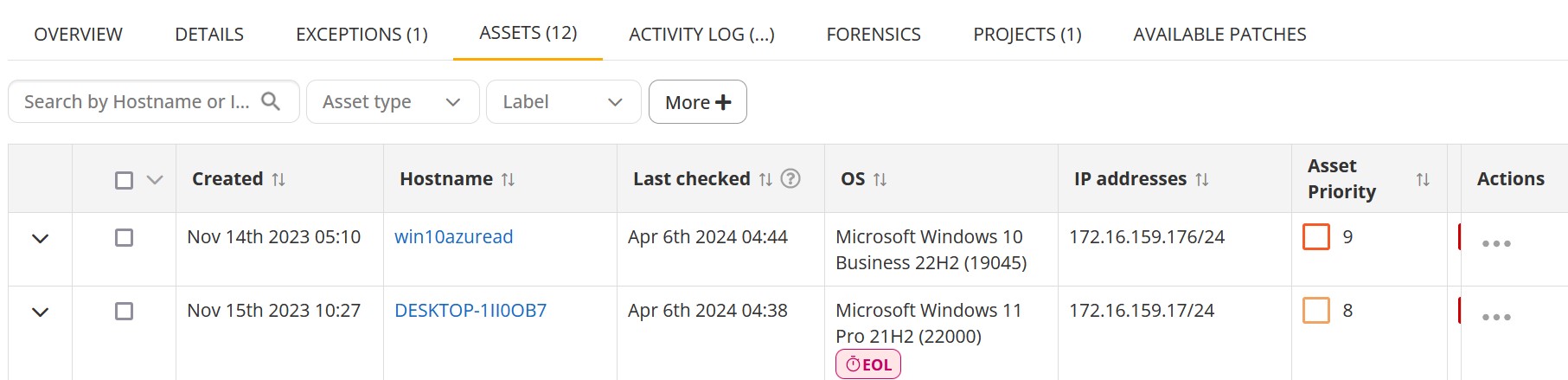
Assets
The Assets Inventory list displays the list of assets on which the issue is detected. Please note, that the Assets tab is not displayed for Identity issues.
The information is displayed in the grid with the following columns:
| Column | Description |
|---|---|
| Created | Date and time when the issue has been first detected on the asset. |
| Hostname | The hostname of the asset. |
| Last Checked | Indicates when the server last received findings related to this issue from the agent or collector. |
| OS | Operating system on the asset. |
| IP Addresses | IP addresses on the local network interfaces on the asset. |
| Asset Priority | The asset priority on a scale of 1-10. |
| Issue Priority | The issue priority on a scale of 1-10. |
| NPS | The Nanitor prioritization score of the issue. |
| Action | Allows adding an asset to exceptions or requesting re-check to verify that the issue has been resolved on this asset. |
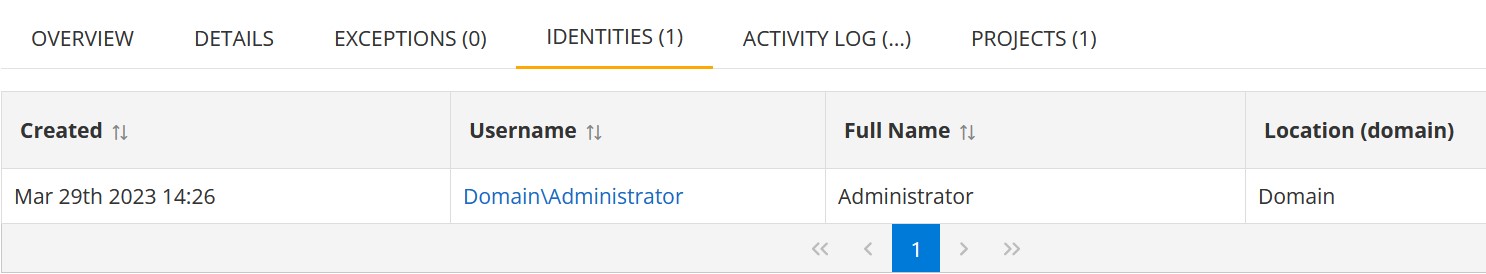
Identities (Identity issues only)
The Identities Inventory list displays details of the identity on which the issue is detected.
The information is displayed in the grid with the following columns:
| Column | Description |
|---|---|
| Created | Date and time when the issue has been first detected on the identity. |
| Username | The username of the identity. |
| Full Name | The full name of the identity. |
| Location (Domain) | The name of the asset (for local users) or a domain name (for Active Directory users). |
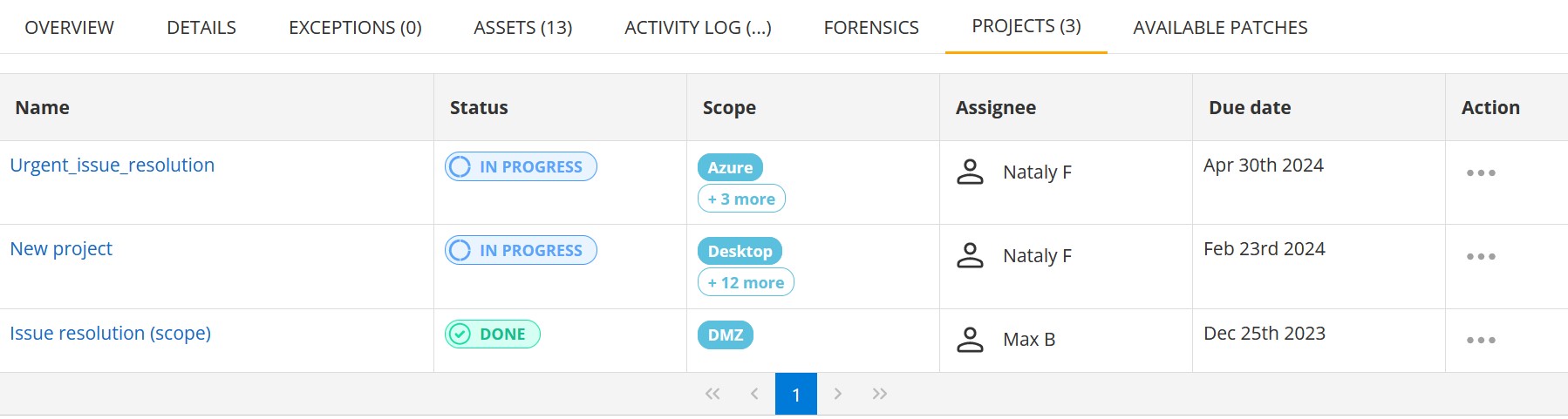
Projects
The Projects Inventory list displays Issue resolution projects to which the issue is assigned.
The information is displayed in the grid with the following columns:
| Column | Description |
|---|---|
| Name | The name of the Project. |
| Status | The status of the Project (Backlog, In progress or Done). |
| Scope | The assets that are within scope for this project. It can be All assets or a list of selected assets and labels. |
| Assignee | The user to whom the Project is assigned. |
| Due date | The date by which the Project must be done. |
| Action | Allows removing the issue from the project. |
Activity log
Log of all events related to the issue. For example, it lists when an issue was detected or removed on a single asset, or when an exception has been added or removed.
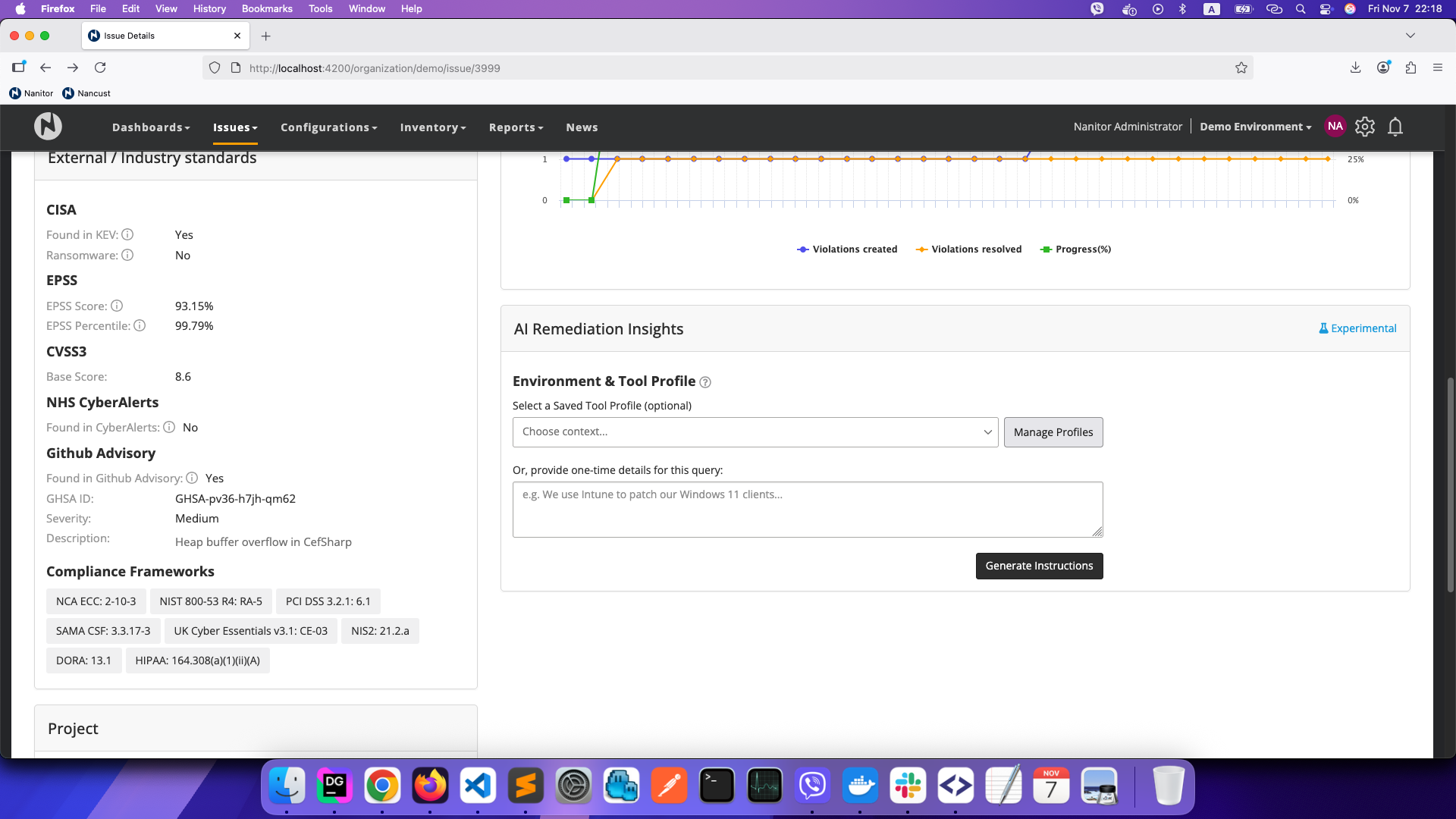
AI Remediation Insights
AI Remediation Insights uses artificial intelligence to generate tailored remediation suggestions for detected issues. This feature helps you understand how to resolve security issues by providing context-aware guidance based on the issue details and your environment.
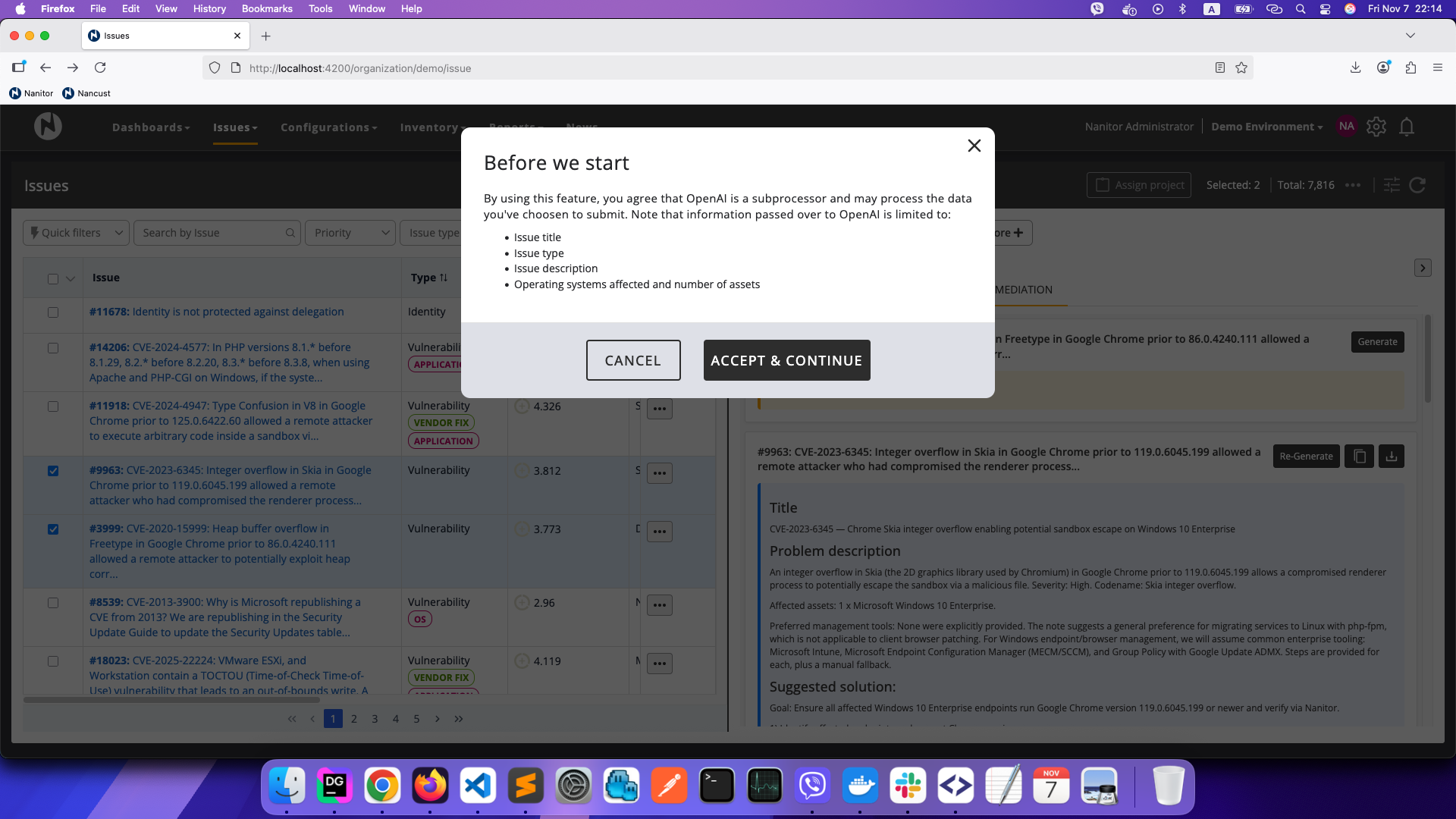
Getting Started
The first time you use AI Remediation Insights, you will be asked to consent to the data processing terms. The consent dialog explains what information is shared with the AI system:
- Issue title
- Issue type
- Issue description
- Operating systems affected and number of assets
Click Accept & Continue to enable the feature. You can manage or revoke your consent at any time from Admin → Account Settings → Privacy & Consents.
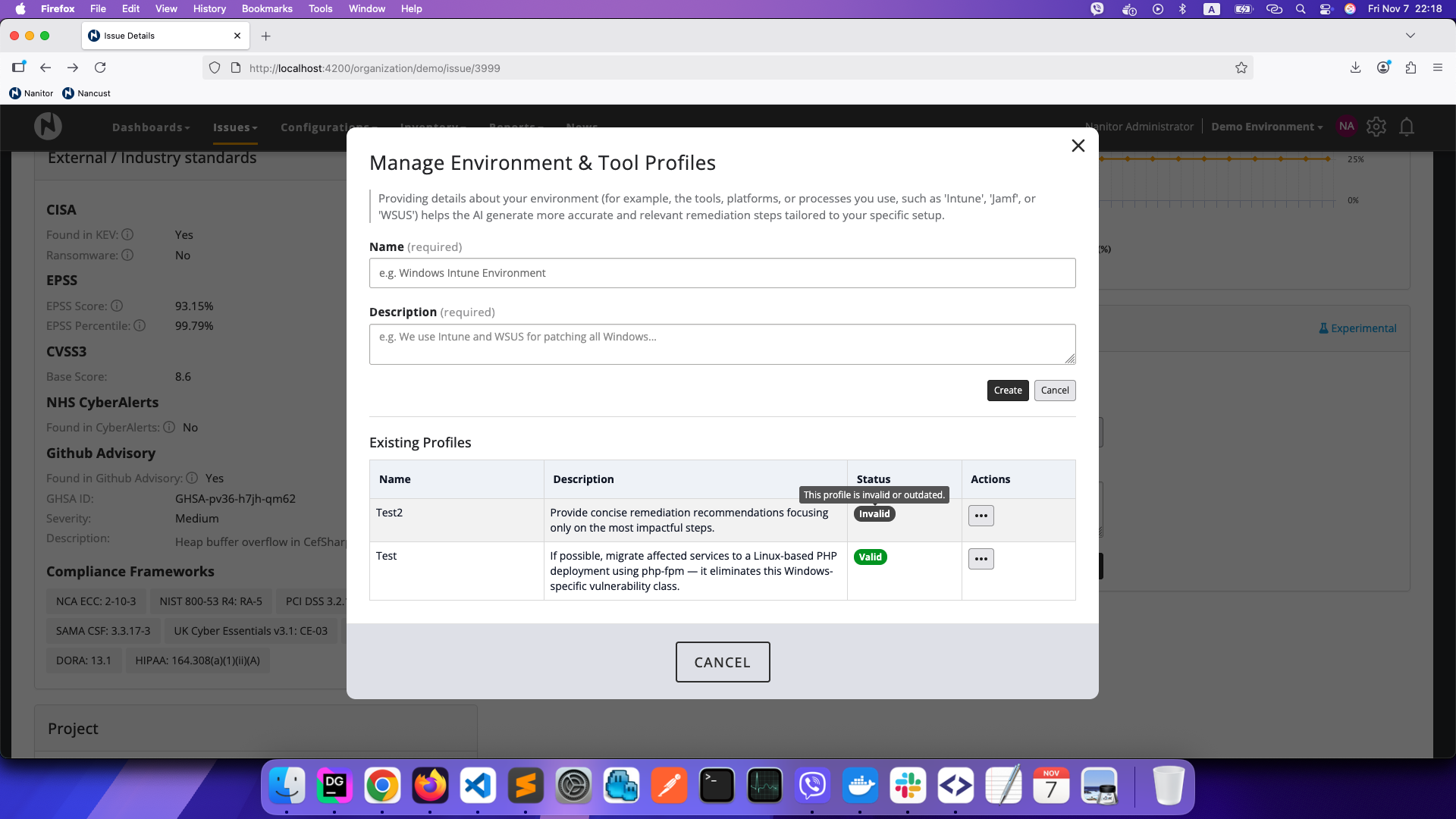
Environment & Tool Profiles
To get more accurate and relevant remediation advice, you can provide context about your environment by creating Environment & Tool Profiles. These profiles describe the tools, platforms, and processes you use (such as Intune, Jamf, WSUS, or other management tools).
To manage profiles:
- Click Manage Profiles next to the profile selector
- Create a new profile by providing a name and description
- Select a saved profile when generating remediation instructions
Profiles are validated periodically. If a profile becomes outdated or invalid, it will be marked accordingly and you can update it.
One-Time Queries
If you don't want to save a profile, you can provide one-time context for a specific query. Simply enter details about your environment in the text area below the profile selector before clicking Generate Instructions.
Using AI Remediation
- Navigate to an issue's detail page
- Scroll to the AI Remediation Insights section
- Optionally select a saved Environment & Tool Profile or enter one-time context
- Click Generate Instructions
- Review the AI-generated remediation guidance
You can regenerate instructions if needed, and copy or download the results for reference.